Deepfake Resilient. NIST Compliant. Proven.
iProov is the first biometrics vendor independently certified to meet the NIST 800-63-4 Digital Identity Guidelines, setting the benchmark for AI-driven fraud protection.

Why iProov?
Science-based biometric solutions drive the highest levels of identity assurance with the best user experience. Powered by liveness and active threat management, iProov assures an individual is the right person, a real person, authenticating right now.
What Makes iProov Unique?
How iProov Keeps Your Identity Systems Secure from Evolving Threats
Our customers benefit from in-house threat intelligence and automated security updates. This ensures you remain protected without the need for in-house maintenance or expertise. Watch the explainer animation to learn more:
iProov Biometric Solution Suite
What problem do you want to solve?
Each solution can be deployed with varying levels of identity assurance to meet your risk appetite.
CERTIFICATIONS MATTER.
- eIDAS Level of Assurance High
- ISO/IEC 30107-3
- SOC 2 Type II
- Certified G-Cloud Supplier
- Federal Reserve SIF Mitigation Provider
- iBeta
- iRAP
- UK National Physical Laboratory (NPL)

Right Person
Real Person
Right Now
What’s New at iProov?
CEN/TS 18099: The Standard That Proves Injection Attack Resilience

Understanding Attack-as-a-Service: The Dark Ecosystem Fueling Identity Fraud
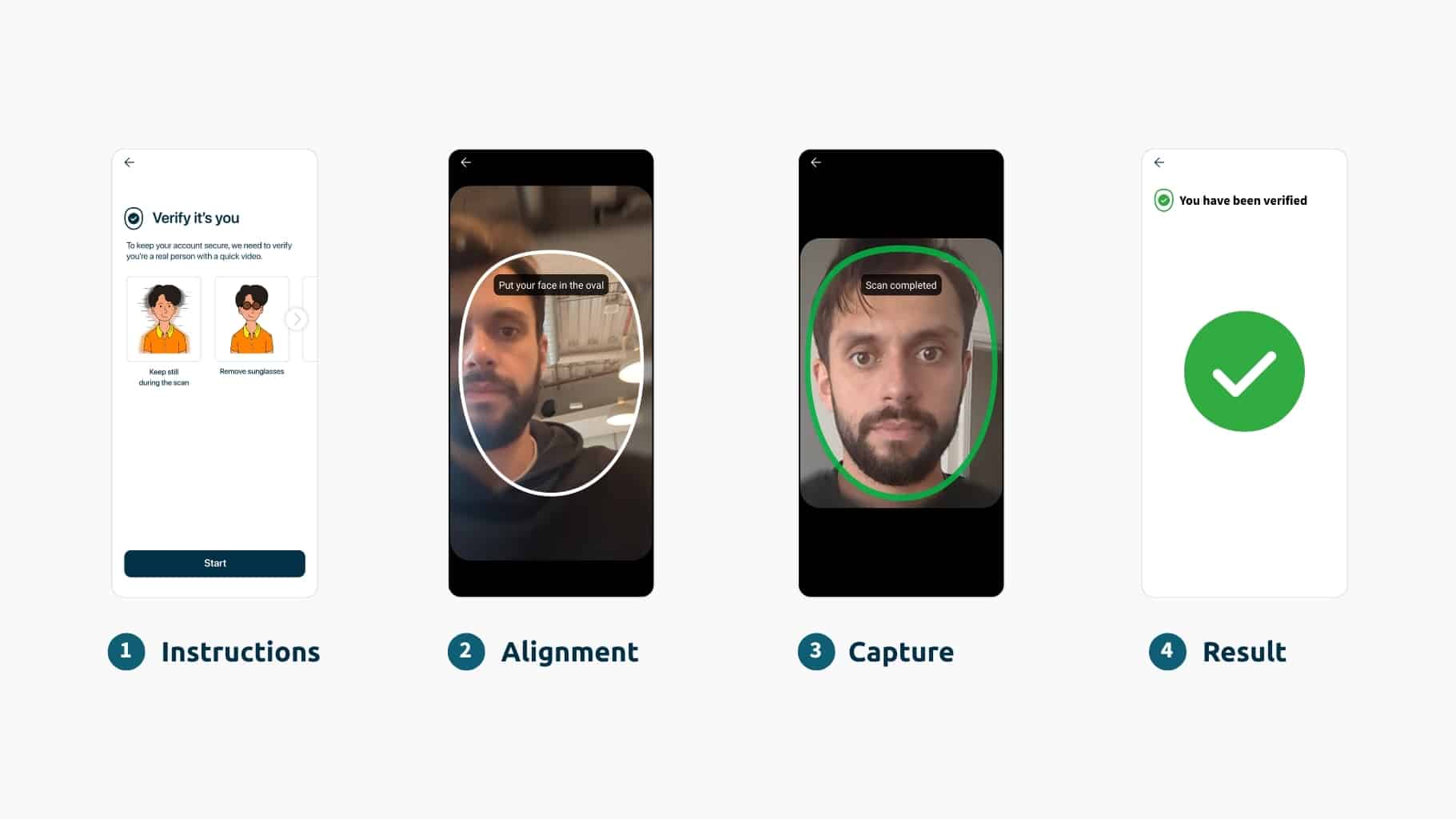
5 Common UX and Performance Challenges with Customer Face Verification (And How to Solve Them)
iProov Threat Intelligence Report 2025
Native Virtual Camera Attacks Surged 2,665%
The latest iProov Threat Intelligence Report reveals alarming trends in remote identity verification:
- Native virtual camera attacks increased by 2,665% in 2024
- Face swap deepfake attacks rose 300% following last year’s 700% jump
- Security experts are now tracking over 120 different face swap tools
- Threat actors are rapidly adopting new technologies to bypass verification systems
Don’t wait until your security is compromised.
Download the 2025 Threat Intelligence Report to understand the evolving threat landscape and discover how to protect your remote identity verification systems.
Trusted By




