December 31, 2023
The Identity Theft Resource Centre (ITRC), a victim-centric non-profit organization, recently released its Biometric Working Group Discussion Paper written by recognized policy, academic, technical, and business experts.
Following the public sector fraud crisis during COVID-19, the ITRC received a surge of complaints, as the world experienced unprecedented levels of identity-based fraud. After diligently researching and analyzing the problem, the group concluded that “biometrics represent the best chance for protecting the identities of individuals as well as improving the integrity of public and private sector process”. In other words, the question is not whether biometric technology should be adopted, but how?
Recognizing that traditional credential-based security methods are failing, organizations have begun to see that biometric-based identity verification is the antidote to cybercrime and fraud.
But not all biometric solutions are the same. The report provides recommendations around what key capabilities a “good” biometric solution should include. In this article, we will provide an overview of what constitutes a robust, secure biometric solution.
The Ever-Increasing Threat of Identity Fraud
Identity fraud is a colossal issue, particularly in America. According to Javelin Strategy & Research, Identity fraud cost $52 billion in loss in the US across 2021. iProov data found that a staggering 29% of Americans have been a victim of identity theft, compared with just 15% of Brits and 13% of Australians. With a new victim every 22 seconds, the scale of the problem is immense.
It is important to note that the ITRC is unsponsored and not a biometric-focussed organization; it operates the largest repository of U.S. data breach information since 2005. Their position is that “data alone can no longer be trusted as the sole source of truth about a person’s identity in most processes”.
The ITRC concludes that biometric-enabled identity verification is now the only reliable method of verifying identity remotely, and therefore better protects customers.
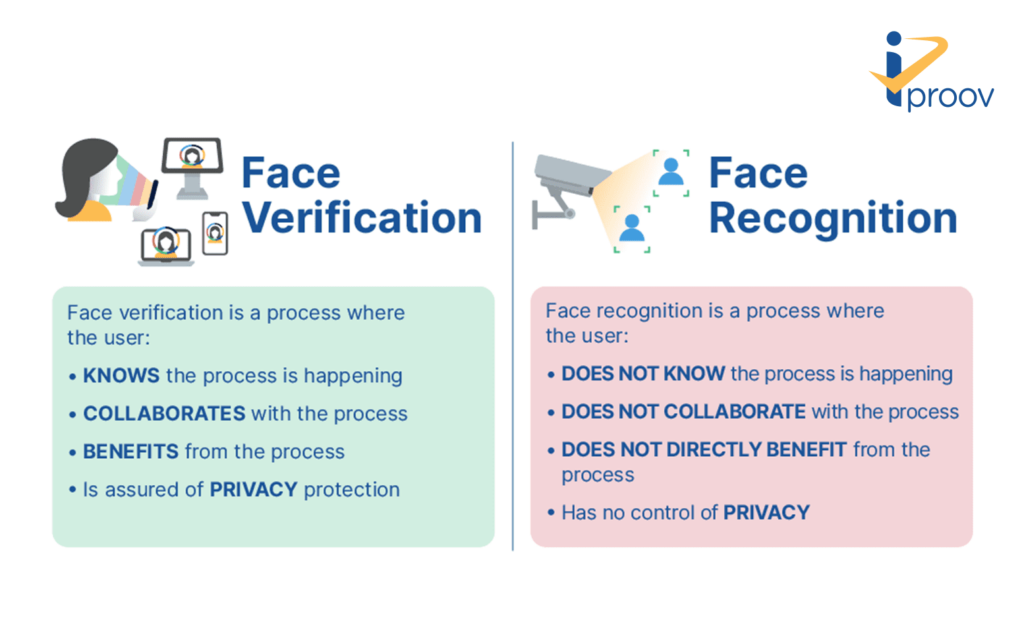
Face Verification is NOT Face Recognition
The report also critically examines how the adoption of facial biometrics has been hampered by its confusion with facial recognition. There are key differences:
- Facial verification is consent-based, unlike facial recognition. Face verification can be privacy-preserving. Face recognition cannot, as the person does not consent to the process.
- Face verification is one-to-one verification that’s beneficial for the user. Face recognition is one-to-many. Its main purpose is to aid law enforcement, but it’s not consensual – it’s trying to find a user in a large database.
- The role of facial verification is asserting identity, using their face to prove that they are indeed that user. It aims to reduce identity fraud, increase accuracy, and provide an inclusive and secure identity verification solution that protects individuals from the growing threats of identity-related crimes.
Ultimately, the distinction between face verification and face recognition is crucial for the adoption and implementation of facial verification technologies. iProov has been underscoring the importance of this distinction for years. You can learn more in this article.
What Makes Biometric Face Verification the Gold Standard For Remote Identity Verification?
By utilizing facial biometrics as part of a comprehensive identity verification process, the authenticity of an applicant can be ensured in a low-risk and equitable manner. This approach reduces the value of compromised Personally Identifiable Information (PII) to bad actors and offers an inclusive solution that goes far beyond what traditional verification methods can offer
Facial verification provides an alternative to legacy identity verification solutions that may rely heavily on credit data, which may exclude individuals with limited or no credit history. This aspect is particularly beneficial for reaching and verifying the identities of individuals who would otherwise face challenges in remote identity verification processes.
You can read more about the advantages of face biometrics here.
Not all Biometric Solutions are Equally Effective
Choosing a science-based solution that can deliver the highest levels of identity assurance and have proven track records with security-conscious organizations is essential.
Let’s examine a few of the criteria that form a robust facial verification system:
- Liveness detection: As the ITRC articulates, the best solutions not only verify the captured image presented, but also determine the “liveness” of the individual and that the individual is real and not a spoof.
- One-time biometric: One-time biometric technology is essential. It verifies that an individual is authenticating in real-time and is not a photo or mask, nor a digitally injected attack using a replay of a previous authentication, or synthetic video (such as a deepfake). Learn more about one-time biometric technology here.
- Active threat monitoring: The report also stresses the importance of active monitoring: “Real or near-real-time monitoring can provide early detection of performance anomalies and enable timely remediation”. iProov provides this through our Security Operations Center (iSOC), which gathers insights into advanced biometric attacks and builds resilience to ongoing threats. We are the only biometric vendor to share our findings in our annual Biometric Threat Intelligence Reports.
Inclusivity and performance:
- Evaluate certifications: The report acknowledges that some biometric solutions are “more accurate than others”, and that some “work better across a diverse population than others, including persons with disabilities”. Look for solutions like iProov’s, which are certified by the National Institute of Standards and Technology (NIST) and is one of the few vendors to achieve full WCAG 2.2 compliance. The biometric vendor should keep up to date with evolving standards, certifications, and conformance.
- Evaluate bias mitigation practices: this is not a one-time endeavor but an ongoing commitment. Transparency, diversity in training data, regular testing, and adaptability are essential components of a robust strategy. Bias mitigation is not limited to age, skin tone, or gender; other socio-demographic impacts, such as access to devices with cameras, need to be considered.
Privacy-protective Considerations:
- Biometric template: The vendor should only store biometric data in an anonymized format, so it’s useless to an attacker. Rather than stored imagery, a biometric template is a mathematical representation of biometric data that cannot be associated with an identifiable person. Ultimately, this bolsters user privacy and data protection. You can learn more about biometric templates here
- Privacy firewall: The vendor should use a technology that uses a privacy firewall, where there’s a structural separation between the user identity and the user’s biometric. All PII is stripped away, leaving only the biometric, which, on its own is useless if leaked or stolen. It’s highly effective in safeguarding the privacy of the user.
- Cloud-based authentication: There are many benefits to cloud-based biometric security. A key one is the protection of user data: cloud security is opaque to an attacker and far more difficult to reverse-engineer.
The report also specifically recommends finding a vendor that has real-time verification capabilities and passive detection techniques. iProov is unique in the identity assurance space, largely owing to its ability to confirm whether a device is sharing correct real-time information about a real user right now.
You can learn more in our guide to choosing a biometric vendor here.
Closing thoughts
Ultimately, ITRC does not recommend any particular vendor but stresses that biometric-enabled identity verification is the “best hope for reducing impersonation crimes in the short and long term”, and that organizations should seek the “best solution for them as soon as possible” to reduce the severe and ever-growing threat of identity crimes.
iProov delivers the most validated face biometric solutions in the world, having been tested to national security standards by the U.S. Department of Homeland Security, the UK Home Office, the Singapore Government, and the Australian Government – often completing over a million verifications per day with pass rates over 98%.
Download the full ITRC Biometric Working Group Discussion Paper here.