March 12, 2025
Establishing trust online has become more crucial – yet more challenging – than ever. How do you replicate the trust of an in-person meeting in a digital environment? This challenge lies at the heart of identity proofing, the foundational process that enables secure digital interactions.
Whether you’re opening a basic account with PayPal or Venmo, accessing government benefits, or verifying your identity for legal documentation, the core requirement remains consistent: establishing trusted digital identities that enable secure remote interactions. While use cases and risk profiles vary, and these scenarios require different levels of assurance, they all depend on solid identity proofing from the outset.
Recent high-profile security breaches highlight the danger and scale of modern attack methods, such as the Knowbe4 incident or Greasy Opal operation. The Federal Bureau of Investigation (FBI) data indicates that identity-related criminal activities generated losses of $8.8 billion in 2023 alone, and another 2024 study uncovered that 75% of organizations have experienced at least one case of deepfake-related fraud.
Identity proofing isn’t merely a compliance requirement, but a business imperative. A key challenge in this digital landscape is ensuring that the person attempting to verify their identity is a real person (i.e. not a deepfake), the right person (matching their claimed identity), and authenticating in real-time.
What’s the Difference between Identity Proofing and Identity Verification?
Identity Proofing Definition
Identity proofing refers to the entire process of establishing and verifying the identity profile of an individual. It involves collecting and evaluating various pieces of evidence – such as government-issued identification documents, biometric data, or personal information – to determine the authenticity and legitimacy of the claimed identity.
Identity Verification Definition
Identity verification is the act of confirming that an individual is who they claim to be. It is a subset of the identity proofing process and focuses on validating the information provided against reliable and authoritative sources. Identity verification involves checking the authenticity and validity of identity documents, comparing biometric data, or verifying personal information against trusted databases. Identity verification aims to ensure that the claimed identity is genuine, up-to-date, and belongs to the person presenting it.
Key Differences:
- Scope: Identity proofing is broader and involves collecting multiple pieces of evidence to establish identity. Identity verification focuses specifically on validating provided information against authoritative sources.
- Analogy: Identity proofing involves constructing a comprehensive identity profile, while identity verification involves performing a precise verification check to support that profile.
Both aim to mitigate the risk of fraud, prevent unauthorized access to sensitive information or systems, and establish a reliable link between a real-world identity and a digital or online persona. Identity proofing is a crucial step in many onboarding processes, particularly in industries with strict regulatory requirements (such as financial services, healthcare, and government, including workforce contexts).
Key Insight: The relationship between verification and proofing highlights a crucial security principle, as identity proofing can only be as reliable as the original identity verification process. For example: if a synthetic identity successfully enters the system during the initial identity check, subsequent verifications – no matter how rigorous – will merely validate this fraudulent identity. This creates a dangerous cascade effect where all future transactions and access decisions are built on a compromised foundation.
Consider the case of Adam Arena, who with his co-conspirators, created a network of synthetic identities to steal over $1 million from banks. They nurtured these false identities for years, building legitimate credit histories before “busting out” – maxing out credit limits and vanishing without a trace. The scheme was so successful that Arena repeated it, targeting the U.S. government’s Paycheck Protection Program during the pandemic. Read more about synthetic identity fraud here.
Ultimately, identity proofing is the comprehensive process of establishing an individual’s identity, while identity verification is a critical act within that process – similar to how Know Your Customer (KYC) is part of the broader Anti-Money Laundering (AML) framework.
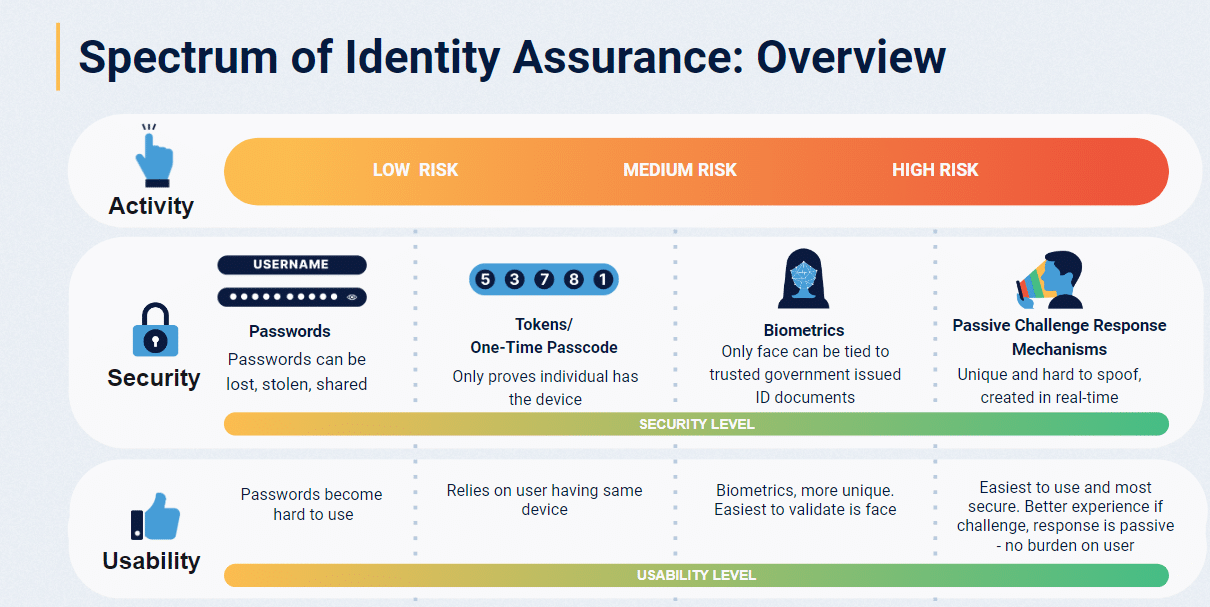
Understanding the Spectrum of Identity Assurance
Identity proofing operates across various assurance levels, as defined by international standards like ISO/IEC 29115. These levels range from basic verification for low-risk scenarios to highly sophisticated methods for critical applications:
- Level 1 (Minimal Assurance): Suitable for accessing basic information or services with minimal risk. Examples include newsletter subscriptions or basic forum access.
- Level 2 (Some Confidence): Appropriate for standard consumer services, such as e-commerce accounts or basic financial services.
- Level 3 (High Confidence): Required for financial services, healthcare, and other regulated industries where identity certainty is crucial.
- Level 4 (Very High Confidence): Essential for government services, high-risk financial interactions/transactions, and critical infrastructure access.
The key is matching the verification method to the risk level — overcomplicating low-risk scenarios creates unnecessary friction, while inadequate verification in high-risk situations exposes organizations to potential compromises.
As organizations move toward higher assurance levels, they must balance security requirements with user experience considerations. This balance is critical to driving adoption while maintaining appropriate protection.
Modern Technologies Enabling Advanced Identity Proofing
Modern identity proofing combines multiple technologies to create robust, user-friendly verification systems:
Document Verification
Advanced document verification uses technologies like OCR (Optical Character Recognition) and NFC (Near-Field Communication) to validate government-issued IDs. This multi-layered approach confirms both the document’s authenticity and its connection to the presenter. Modern systems can detect security features, analyze printing patterns, and validate cryptographic signatures, providing comprehensive document authentication. Learn how iProov works with partners such as Microblink to keep up with evolving fraudsters, combatting Generative AI and document-based biometric attacks.
Database Verification
Cross-referencing provided information against trusted databases adds another layer of validation. While this method shouldn’t be relied upon alone, it can confirm the consistency of identity information across multiple sources and flag potential discrepancies for further investigation.
Biometric Verification
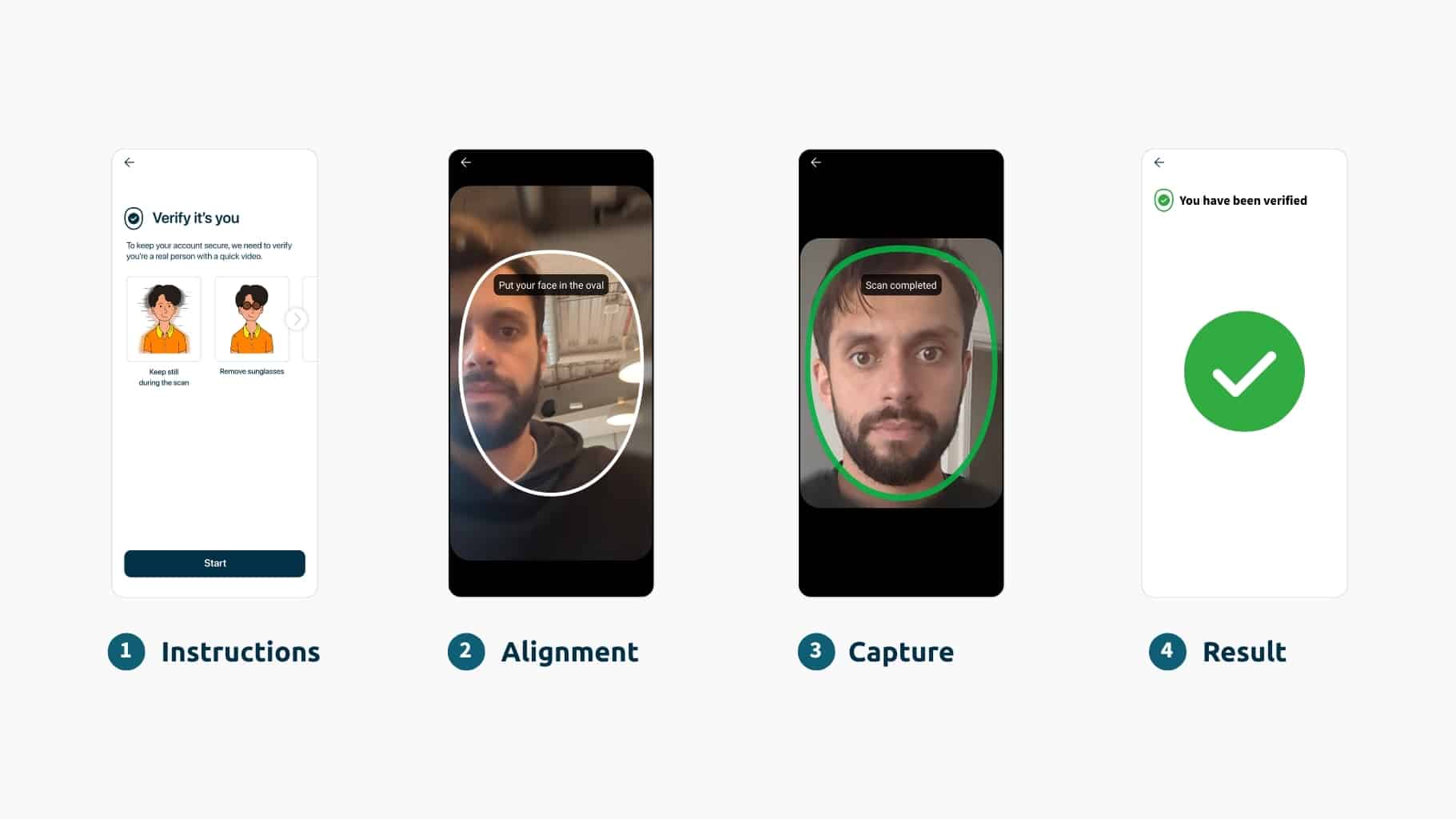
Facial biometrics with science-based liveness detection are the cornerstone of remote verification. They ensure that the person behind the screen is genuine and matches their claimed identity. This technology provides a powerful defense against sophisticated spoofing attempts, including deepfakes, face swaps, and digital injection attacks. Advanced algorithms can detect subtle signs of manipulation, ensuring that the person presenting the biometric is physically present, alive, and the right person.
Future Trends and Innovations
Unfortunately, identity proofing is often implemented as a one-time process during user onboarding. However, best practices suggest incorporating periodic re-verification to ensure the identity remains valid over time. This is especially important at high risk inflection points in the user lifecycle such as:
- Account resets and dormant account reactivation
- Unusual login attempts or user behaviour
- Significant account changes
- Authorizing large transactions
- Privilege escalation
- Accessing particularly sensitive data or functions.
Moments like these represent opportunities for fraudsters to exploit vulnerabilities in identity systems.
Biometrics and secure digital identity systems play a crucial role in these processes, allowing for more seamless and secure ongoing verification.
The identity proofing landscape continues to evolve with:
- AI and Machine Learning: Enhanced fraud detection and risk assessment, including solutions that can keep pace with the evolving threat landscape
- Decentralized Identity: Self-sovereign identity solutions
- Continuous Authentication: Moving beyond point-in-time verification
- Zero Trust Architectures: Assuming no identity can be trusted without verification
These are contextual, basic overviews of complex topics that we expand upon in depth in our Spectrum of Identity Assurance series. This theme explores key identity proofing trends, challenges, and innovations across this blog series.
As organizations continue their digital transformation journey, strong identity proofing becomes increasingly critical. By implementing sophisticated verification systems that balance security with usability, organizations can build trust, prevent fraud, and create seamless digital experiences for their users.
Want to see how iProov can help secure and streamline your identity verification processes, providing a frictionless user experience that builds customer confidence and loyalty? Book a demo today and see the difference our biometric solutions make yourself!