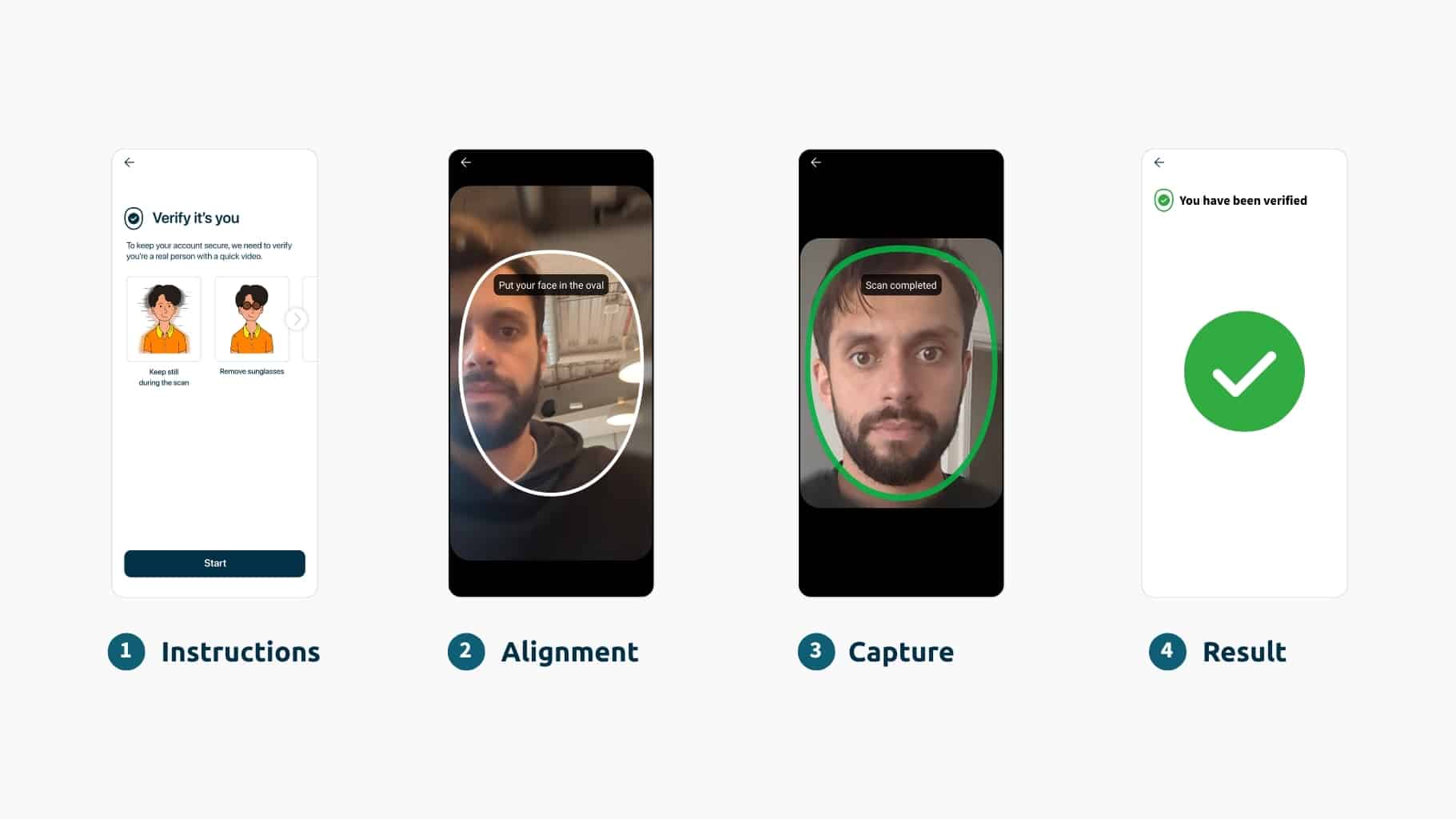
April 26, 2024
The world is digitizing at an incredible pace, and traditional authentication methods, such as one-time passcodes, are failing to keep organizations secure. As fraud technologies and methodologies grow in sophistication and scale, facial biometric verification has emerged as one of the most secure and convenient methods for organizations to verify user identity online.
However, organizations must understand that not all facial biometric technologies have kept up with the rapidly changing threat landscape. Not all are equal in the level of security, resilience, or adaptability to novel threats.
Deploying a facial biometric verification solution without having visibility over threats and how they evolve is like building a house without the right materials to withstand the elements. To be effective, solutions must be resilient to the ever-evolving threat landscape and utilize threat intelligence to ensure that they can provide the expected level of identity assurance.
Understanding Trends in Biometric Attack Types
Recently, iProov published an industry-first Biometric Threat Intelligence Report, in which threats to in-production biometric technology were analyzed across the last year. Download the threat report here for all insights and data.
For now, we’ll highlight a key discovery:
There was a sharp increase in face swaps and digital injection attacks across 2023
We observed an increase in face swap injection attacks of 704% H2 over H1 2023. Injection attacks are rapidly evolving with significant new threats to mobile platforms. We saw an increase of 255% in injection attacks against mobile web H2 over H1 2023.
*For more details on our methodology, visit the 2024 Threat Intelligence Report.
What is the difference between digital injection attacks, face swaps, and presentation attacks?
Presentation attacks involve presenting an artifact – such as a printed photo, silicone mask, or deepfake video on a screen – to a cell phone or computer. Presentation attacks have a long history and are generally well-understood.
Digital injection attacks, on the other hand, are sophisticated, highly scalable, and replicable cyberattacks that bypass the camera on a device (or are injected into a data stream). They are far more scalable than presentation attacks, and they do not require the manual creation of a physical artifact or any physical presentation. This scalability drives the higher frequency and danger of digital injection attacks.
Face swaps are a type of synthetic media created from two inputs that ultimately superimpose another identity over the original feed – “swapping” two faces in real time. Face swaps derived from generative AI are the primary concern due to their ability to manipulate key traits of images or videos.
Many biometric solutions are not equipped to defend against evolving and unmapped threats like face swaps and digital injections. In response to the ever-evolving threat of systemized and scalable attacks, security needs to be resilient and adaptive – rather than simply resistant to established and known spoofs.
Why Is This Important?
The need for secure, remote identity verification is higher than ever. Organizations need to know that their new and returning users are genuinely who they claim to be.
But manual remote identity verification has been proven ineffective, and the threat landscape is evolving. Innovative bad actors are using advanced tools to create new and widely unmapped threat vectors. All remote verification methods are vulnerable to synthetic media tools such as face swaps, whether entirely human-operated video calls, hybrid processes with facial biometric checks and human oversight, or fully automated.
Ultimately, those leveraging biometric verification technology are in a stronger position to detect and defend against attacks. But you need to choose the right biometric solution…
Why Listen To Our Recommendations?
iProov is widely regarded as a pre-eminent provider of facial biometric technology solutions, trusted by prominent organizations across the globe, including the Australian Taxation Office (ATO), GovTech Singapore, UBS, ING, the UK Home Office, the U.S.Department of Homeland Security (DHS), and many others.
How We Secure Our Biometric Solutions
Given the ever-transformative nature of generative AI and the scalability of digital injection attacks, it is imperative that biometric security be actively managed and adaptive.
One key element in our security process is iProov Security Operations Center (iSOC) – the industry-first global threat intelligence and active threat management system. Through iSOC, iProov monitors traffic in real-time to detect attack patterns across multiple geographies, devices, and platforms.
This enables continuous monitoring and learning from attack sources, patterns, and methodologies, keeping our biometric systems one step ahead of the evolving threat landscape.
Having full visibility of threat development is crucial because once attack tools or methodologies are successful in breaching systems, they are often quickly shared – typically on the dark web or within Crime-as-a-Service networks – which means they can scale very quickly. You can read more about real-world examples of this in our LATAM Deepfakes Report.
If you do not have visibility of attack types, it makes it very difficult to prioritize which spoof types to mitigate against and doesn’t allow an understanding of how the attack behavior is changing. Visibility is crucial for long-term, dynamic defenses.
iSOC delivers:
- Transparency: Attacks are spotted and investigated quickly.
- Security: We continuously learn and stay ahead of future attacks while maximizing platform performance.
- Satisfied customers: Customers benefit from ongoing security and active threat management, affording greater peace of mind.
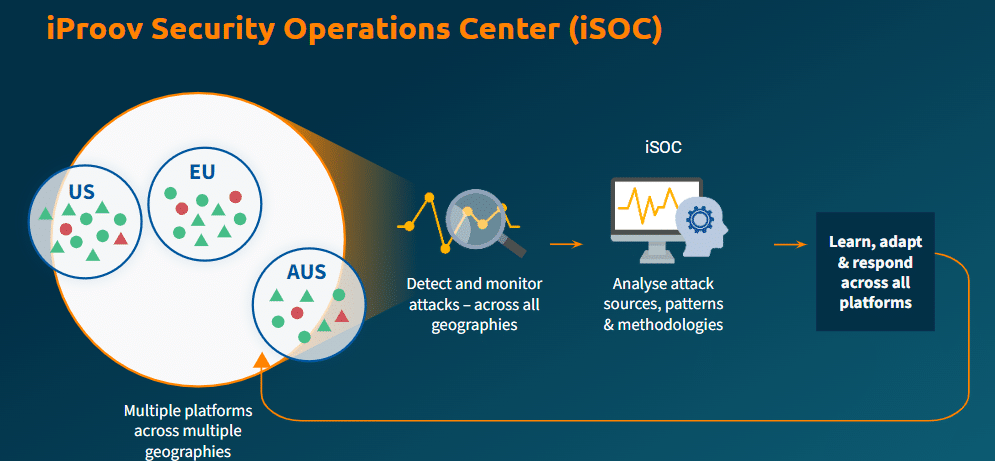
This ultimately helps to protect your users and your organization from future and as-yet unknown threats.
The Cloud is Critical For Ongoing Security and Rapid Response
Security systems also need to be able to implement fixes quickly in order to outpace threat actors and maintain ongoing protection.
That’s where cloud-based technology comes in:
- Verification happens in the cloud: All verification attempts happen in the cloud rather than on the device. If an attacker manages to physically or digitally compromise a device with ransomware, for example, the verification remains unaffected because it is separated from potential vulnerabilities on the device.
- The cloud powers iSOC: iProov is able to monitor and analyze attacks on our systems in real time because we verify within the cloud. This means full visibility over the execution environment.
- Updates can be rolled out quickly: Cloud-based SDK deployment means that if platform updates need to be rolled out in response to a certain threat, they can be done server-side rather than devices being updated manually. Defenses and algorithms can be updated continually, which can make life much harder for attackers.
Unique Passive Challenge-Response Mechanism Ensures Real-Time Authenticity
Sophisticated threats, such as deepfakes, can often successfully emulate a person verifying themselves, which many liveness technologies cannot spot. Advanced verification methods are needed to secure against advanced threat types.
How does our challenge-response technology work? The user’s device screen illuminates their face with an unpredictable sequence of colors. We analyze the reflections of that screen light from the user’s face. The way that the light reflects and interacts with the face tells us whether it is a real-life, three-dimensional human or not.
The sequence of colors that we see reflecting from the face must be the sequence that we told the device to flash. If it looks realistic, but the color sequence is wrong, we know we’re looking at a spoof.
Once used, it can’t be replayed by a person attempting to use a previous verification to spoof the system. It’s worthless if stolen because the sequence is unique and is obsolete as soon as it’s used. The process is exceedingly user-friendly and entirely passive.
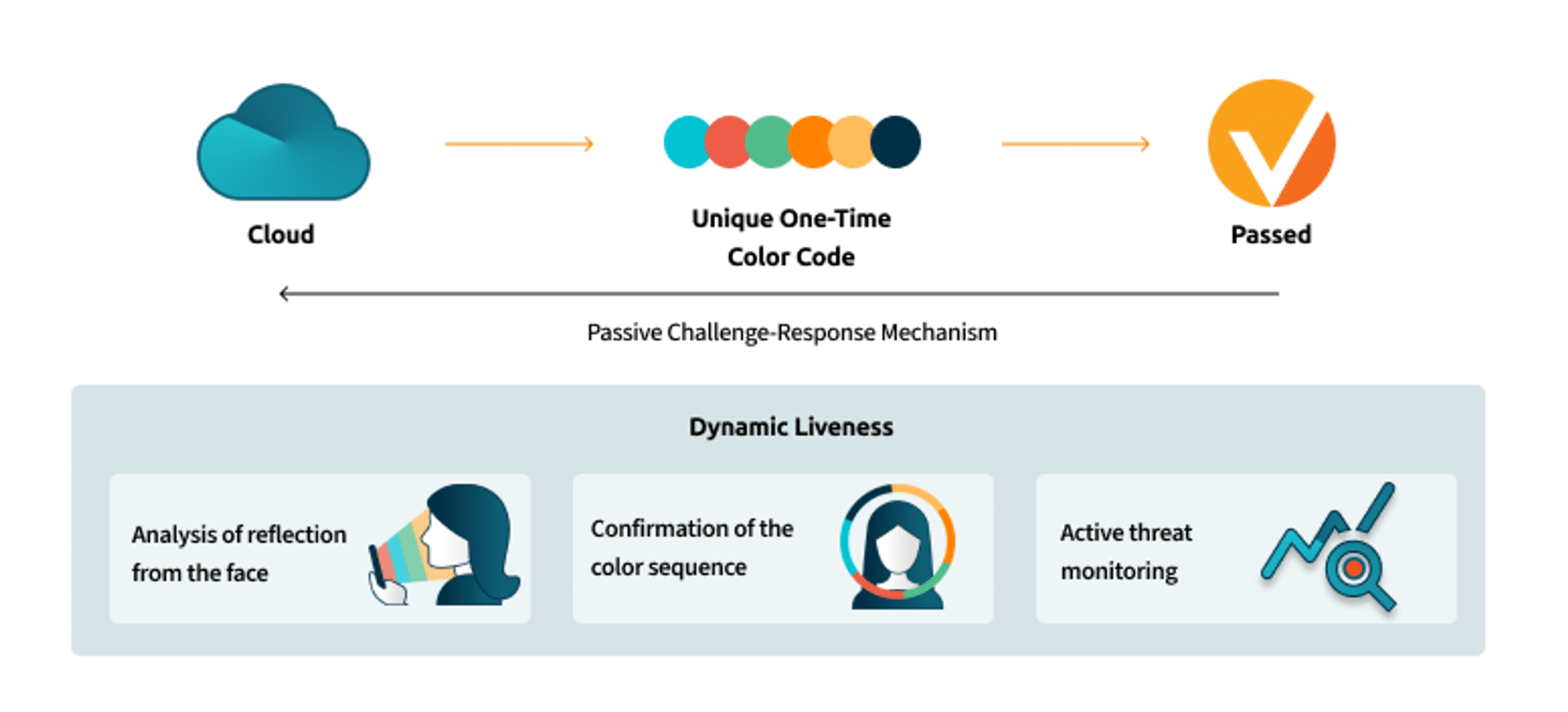
Ultimately, because the threats are constantly evolving, it’s essential to understand the threat landscape and make decisions based on real-world, in-production intelligence. iProov employs the discussed technologies – iSOC, cloud-based verification, and unique passive challenge-response technology, amongst others – to deliver the solution of choice for the world’s most security-conscious organizations. You are secured and reassured, and active threat management is in place to defend against new and yet unknown threats.
To read more about the key attack technologies and methodologies witnessed by iSOC: download our report, ‘ iProov Threat Intelligence Report 2024: The Impact of Generative AI on Remote Identity Verification’. It highlights previously unknown patterns of biometric attacks that can help organizations make more informed decisions on biometric technology selection. Read the full report here.