February 5, 2026
The democratization of cyberattacks is a worrisome trend. Technology and methodologies that were once the domain of highly skilled actors have become accessible to almost anyone with minimal technical expertise and the ability to navigate dark web marketplaces. This transformation is particularly evident in identity verification attacks, where the rise of these services has fundamentally altered the threat landscape.
This article explores how Attack-as-a-Service (AaaS) has transformed identity fraud, reveals the inner workings of this criminal ecosystem, and provides essential insights to help organizations protect themselves against this evolving threat
What is Attack-as-a-Service?
Attack-as-a-Service represents the commercialization and democratization of cyberattack capabilities. Much like legitimate Software-as-a-Service (SaaS) offerings, these platforms provide ready-made tools, infrastructure, and even customer support for executing sophisticated attack techniques that are available for purchase or through a subscription.
In the context of identity verification attacks, our Threat Intelligence Report reveals a thriving ecosystem of communities specifically targeting remote identity verification systems. These groups have evolved from isolated forums sharing basic techniques into sophisticated marketplaces offering comprehensive attack solutions.
Rather than selling simple software tools, many providers now offer end-to-end services, handling all technical aspects of creating verification bypasses. Customers can purchase these services in two main ways:
- Service-based: Paying for specific technical services (such as having photos processed into convincing face swaps)
- Volume-based: Purchasing a set number of pre-verified accounts or identities ready for use.
One person might pay for a specific deepfake to be created, while another will purchase a few onboarded accounts. This business model offers significant advantages for threat actors, including reduced exposure to security monitoring, control of proprietary techniques, and secure transactional relationships with other fraudsters.
Understanding the Broader Crime-as-a-Service Landscape
Attack-as-a-Service for identity verification bypass is a specialized subset within the larger Crime-as-a-Service (CaaS) ecosystem. While these services zero in on bypassing identity verification systems, the broader CaaS landscape covers a wide range of criminal activities, from credential theft and money laundering to document forgery and other cybercrimes.
This interconnection enables criminals to combine services to execute multi-stage fraud operations. Notably, our Threat Intelligence Report highlights a concerning trend: previously isolated regional groups are now collaborating across borders, mirroring the global structure of legitimate business networks.
The Growing Ecosystem: By the Numbers
The iProov Security Operations Center (iSOC) identified 31 new online threat actor groups in 2024 alone, bringing the total number of tracked communities to an alarming level.
The scale of this ecosystem is remarkable:
- 45% of these groups develop and sell their own attack tools
- 55% focus on reselling or providing related services
- The ecosystem encompasses 34,965 total users
- Tool sellers attract the majority (68%) of users, serving 23,698 individuals
- Nine groups have over 1,500 users, with the largest reaching 6,400 members
These communities aren’t just growing in size – they’re becoming increasingly sophisticated and specialized. Common discussions center on techniques such as KYC bypass methods, the use of deepfake technology for synthetic identities, and platform-specific tools.
The Fraud Service Menu: What’s On Offer
The services available through these marketplaces have evolved far beyond simple tools. Today’s offerings currently tracked by iProov include:
1. Technical Tools and Infrastructure
- Face swap applications: Over 130 monitored by iProov, and growing
- Virtual camera software: 90+ tools
- Mobile emulators: Including location spoofing capabilities
- Metadata manipulation tools
2. Operational Services
- ID farming: Generation and validation of synthetic identities (learn more about the recent major dark web identity farming operation iProov uncovered here)
- Cryptocurrency exchange accounts or KYC bypass tools (learn more in our new Crypto eBook)
- Step-by-step tutorials: For bypassing specific verification systems. Bad actors sell the “recipes” for targeting your orgorganzation and platforms.
- Custom development services: Tailored to target particular organizations
3. Advanced Attack Methodologies
- KYC verification bypass techniques: Leveraging vulnerabilities in identity checks (read more on identity verification)
- Deepfake creation services: Dangerously lower the barrier to entry for sophisticated deepfakes, often used to target static liveness checks (yet ineffective againsta advanced solutions like dynamic liveness)
- Image-to-video conversion: For generating synthetic identities
- Combined attack chains: Designed for specific financial institutions
4. Intelligence Sharing
- Vulnerability information: Insights into susceptible systems
- Successful attack methodologies: Documented and shared within the community
- Target lists: Highlighting systems with weak verification mechanisms
- Real-time updates: Alerting to changes in security measures
What Drives The Digital Underground Economy?
What makes these communities particularly dangerous is their efficient, enterprise-like business model. They maintain reputations, offer customer support, and continually refine their services based on user feedback.
With identity-related fraud generating billions in annual losses (an estimated $8.8 billion in 2023 according to FTC data), even a small slice of these proceeds creates a lucrative market for attack tool developers. This financial incentive drives continuous innovation, specialization, and collaboration within the ecosystem.
Current Targeting Patterns
Targeting is strategic and intelligence-driven. Attack operators actively profile verification systems and share insights on which are most vulnerable.
Systems that effectively repel attacks quickly gain a reputation for being difficult targets, causing threat actors to shift their focus elsewhere. This “Low Attack Rate Paradox” means that the most secure systems often see the fewest attacks.
The Democratization Effect
Perhaps the most concerning aspect of this phenomenon is its role in lowering the technical barrier to entry, something we’ve been warning against in previous iterations of our threat intelligence reports. Individuals with minimal technical knowledge can now execute sophisticated attacks that once required deep expertise. This has several implications:
- Increased Attack Volume: A larger pool of potential attackers leads to more frequent attempts.
- Wider Target Range: Organizations previously considered low-risk now face sophisticated threats.
- Faster Exploitation: New vulnerabilities are quickly commoditized and exploited.
- Unpredictable Patterns: Less experienced operators may inadvertently use tools in novel ways that bypass traditional detection methods.
Defending Against These Threats
Countering this emerging threat demands a fundamental shift in security strategy. Traditional static defenses and periodic updates are no longer enough. Organizations must adopt:
- Continuous Monitoring: Implementing real-time detection and response capabilities as part of an overall security strategy. For a deeper dive on continuous and adaptive biometric security, see here.
- Adaptive Security Measures: Developing defenses that evolve alongside emerging threats.
- Threat Intelligence Integration: Actively monitoring trends and threat actor communities, as detailed in our Threat Intelligence Report.
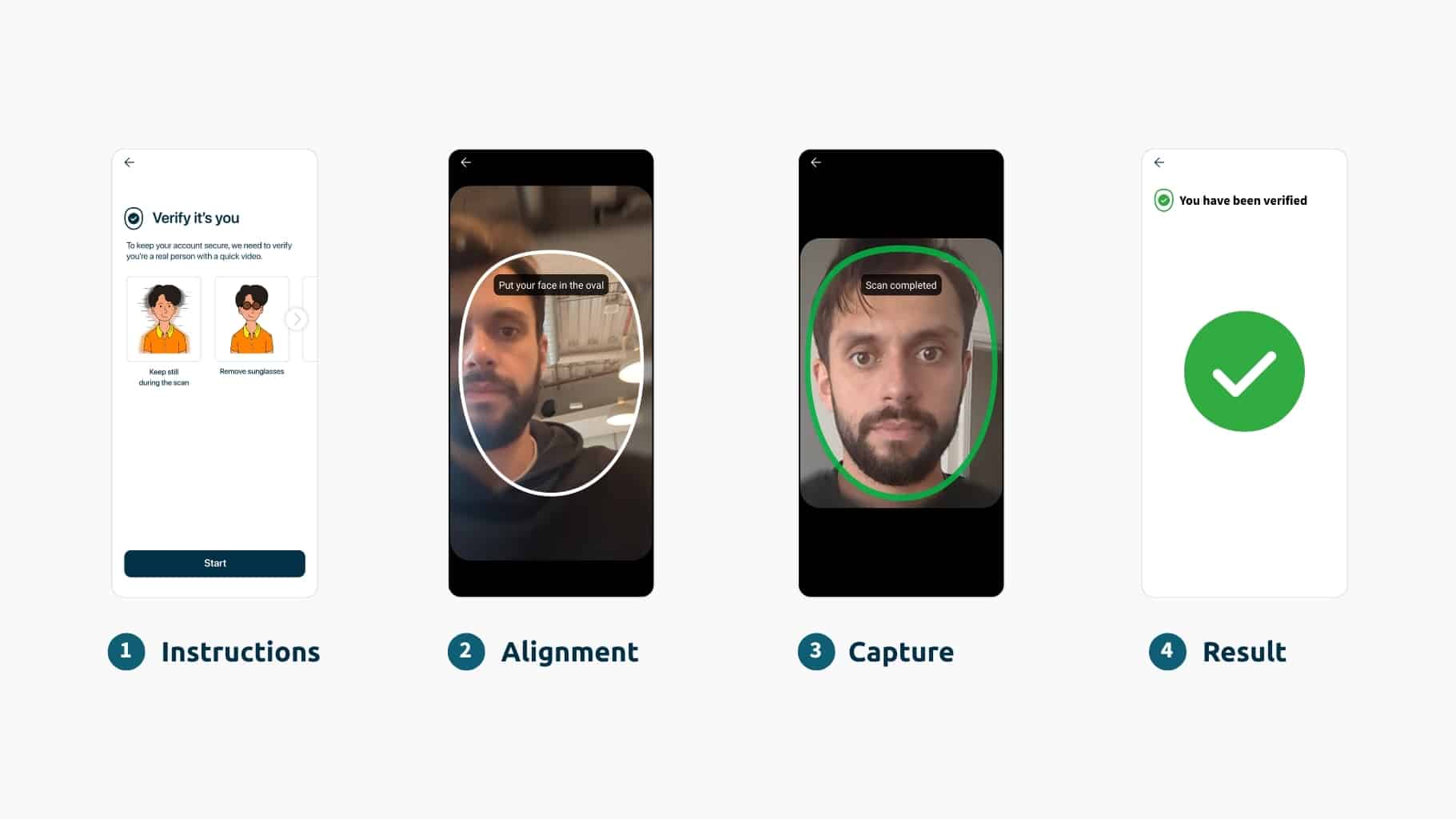
- Multi-Layer Verification: Deploying systems that validate dynamic liveness, not just static proofs of life (learn more about our dynamic liveness technology).
Closing Thoughts on the Attack-as-a-Service Ecosystem
The ecosystem supporting these attack services shows no signs of slowing down. As legitimate AI technologies advance, so too will the sophistication of attack capabilities.
The rapid commercialization of these technologies means that new innovations are quickly packaged and deployed. Organizations must therefore prepare not only for the inevitability of such attacks but also for their increasing agility and speed of evolution.
Success will depend on continuous monitoring, real-time response, and security measures that evolve as quickly as the threat landscape itself.
- Download iProov’s complete 2025 Threat Intelligence Report for a comprehensive analysis of this ecosystem and detailed recommendations for safeguarding your organization.
- Book a demo with iProov today to see how our dynamic liveness technology can help protect your organization against the rising tide of these advanced threats.