September 20, 2024
Remote identity verification is crucial for securing online accounts and transactions in our increasingly digital world. However, balancing security with user convenience presents a significant challenge. Traditional methods like passwords become increasingly vulnerable and unsuitable, while overly stringent processes can alienate users.
Industry experts Paul Jackson and Joe Palmer from iProov recently held a webinar on the ‘spectrum of remote identity assurance’ to address this dilemma. This article distills key insights from their discussion and explores how organizations can optimize the balance between security and usability.
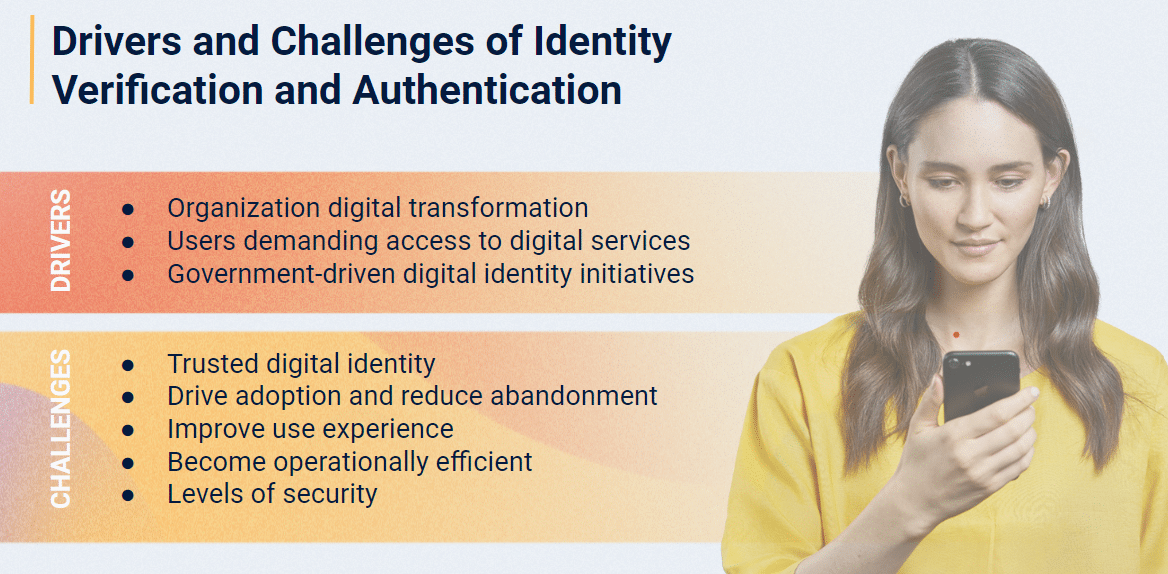
The Drivers and Challenges of Remote Identity Verification
The world is rapidly embracing digital transformation, with businesses and governments moving their processes online. As Joe Palmer explained, “There are digital transformation programs going on across all industries. Governments and enterprise businesses of all kinds are creating digital versions of their previously manual or non-digital processes.”
However, this shift towards digital identity has its own challenges. Trust, user adoption, user experience, operational efficiency, and defining appropriate levels of security are critical considerations. “How do we establish a framework for trusting digital identities?” Palmer questions; “you need to find a way to drive adoption… and ensure the solution is operationally efficient.”
What is The Spectrum of Identity Assurance?
Remote identity verification and authentication exist on a spectrum, with the appropriate level of assurance depending on the risk and context. Low-risk scenarios may only require a username and password, while high-risk transactions demand more robust security. In other words, different risk profiles demand suitably tiered security measures.
Traditionally, identity factors have been split into 3 categories: knowledge, possession, and inherence:
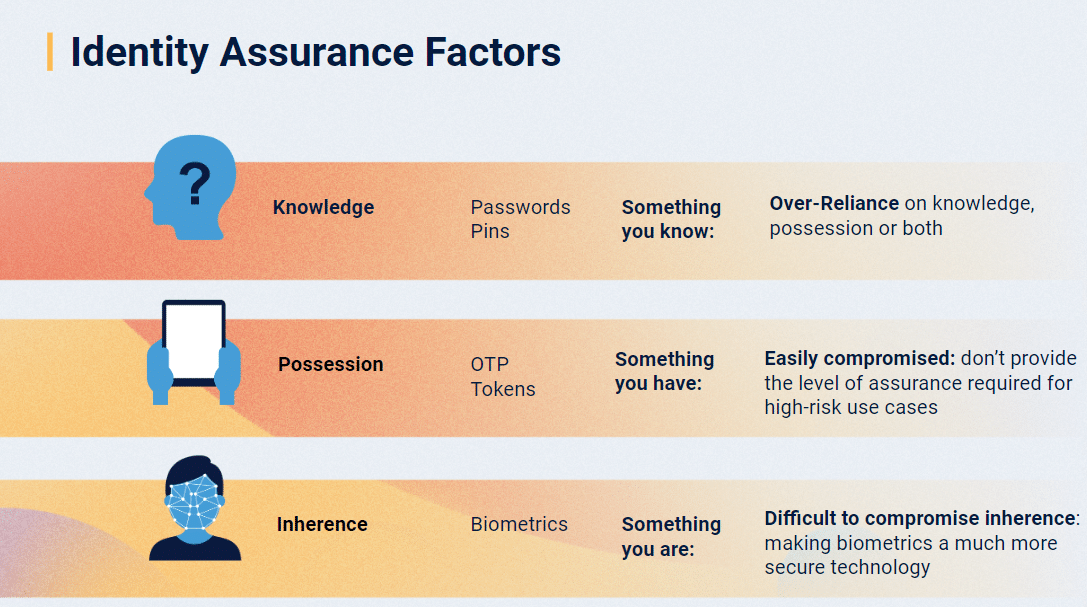
Verifying identity digitally cannot be expressed as a binary “yes”/”no” – no matter which factor you’re using. It can only be expressed in the level of certainty you have in the validity of that identity.
As Palmer stated, “The definition of ‘good enough’ is dependent on many aspects.” A simple username and password combination may work for low-risk scenarios, while multi-factor authentication with biometrics will be needed for high-risk transactions.
Paul Jackson emphasized the importance of the consequences of compromise when you need to determine the appropriate level of assurance: “One way to think about it is the consequence of compromise – how bad would it be if an attacker were to trick the system to successfully impersonate the victim and gain access or trigger that transaction?”
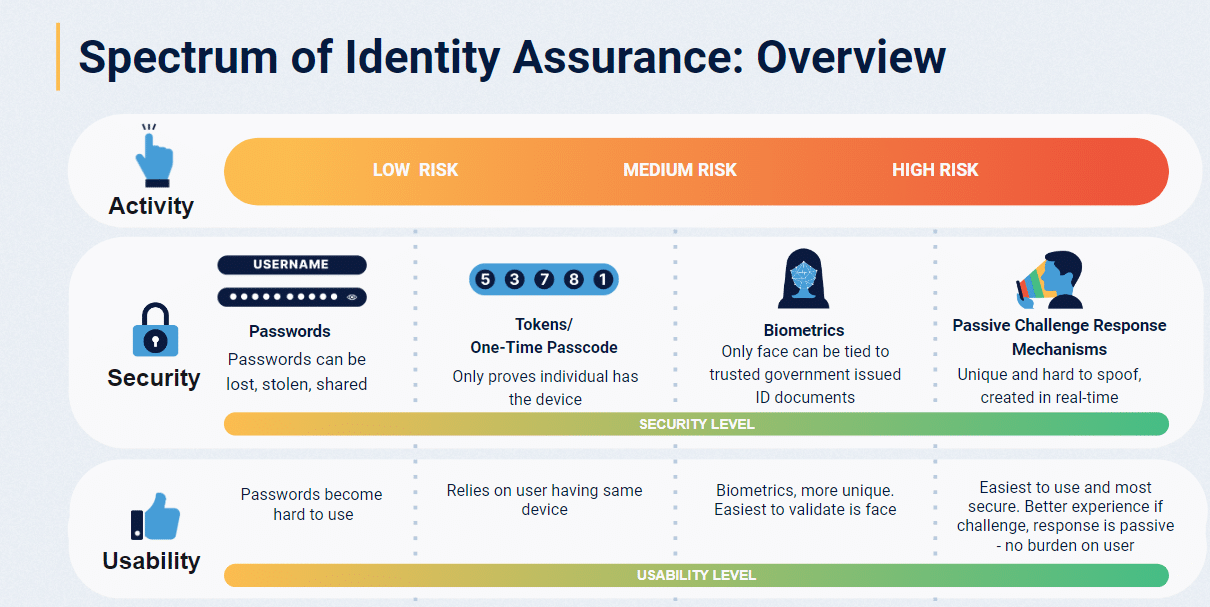
For example, higher-risk use cases and industries (such as making high-value bank transfers or signing up for a critical government service) will require the highest level of certainty that someone is who they claim to be – because there’s so much at stake if you get it wrong.
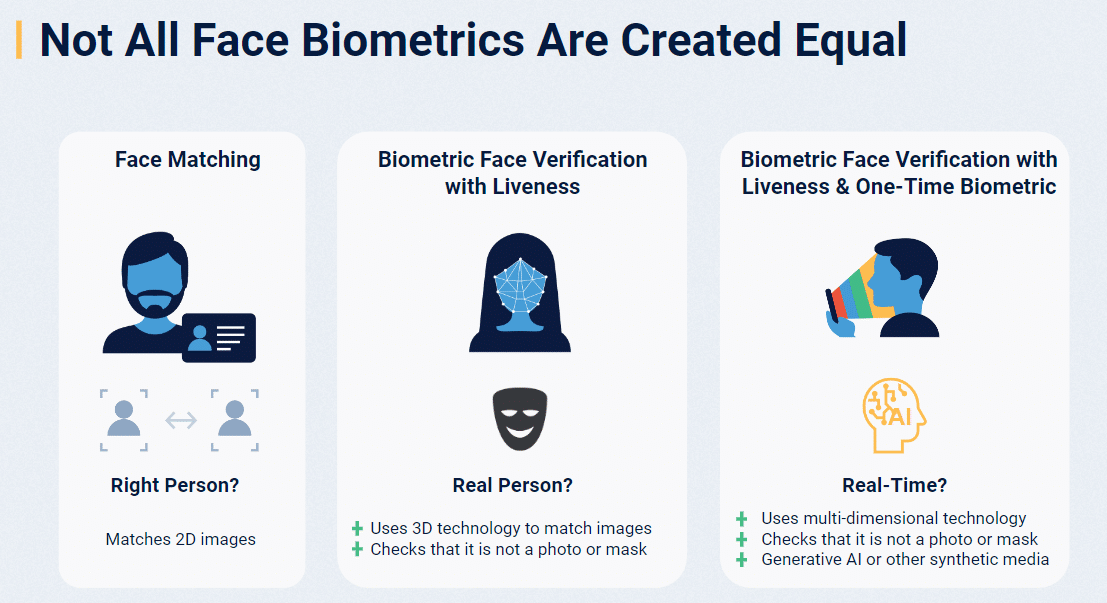
Today, biometric verification (particularly face verification, as the face can be matched against a trusted identity document at scale) occupies the most robust and assured end of the identity assurance spectrum.
As you can see, technologies that were once thought of as secure, quickly fall behind with the pace and sophistication of threats. Biometric authentication solutions that can confirm it’s really you, live and in real-time, offer the most secure method of verifying a person’s identity.
Ultimately, what truly elevates and differentiates biometric solutions is the quality of liveness detection.
Liveness Detection: The Key to Trusted Biometrics
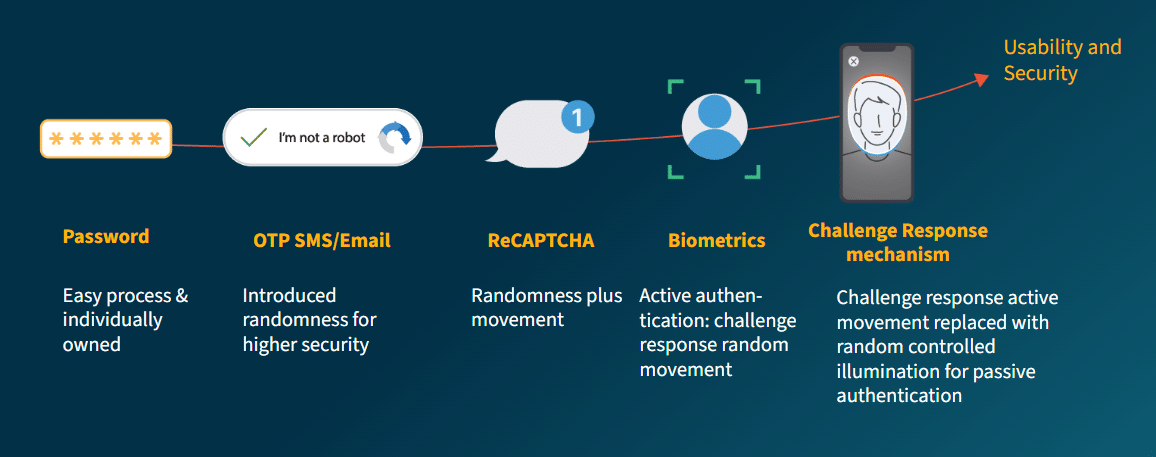
Liveness detection uses advanced techniques to determine if the biometric sample is being captured from a living human at that moment – not a recording or synthetically constructed spoof. This is critical for trusted remote authentication.
Basic liveness techniques analyze single image/video frames for invalid artifacts, detecting presentation attacks like printed photos – but this is rarely enough to stop a motivated bad actor.
“For high-risk scenarios, we want to create a unique challenge-response mechanism,” Palmer stated. “Every authentication becomes unique, and synthesizing a biometric attack in real-time is incredibly difficult.”
A challenge response can be active or passive.
- Active challenge-response mechanisms request that the user perform an action like blinking, smiling, or nodding when prompted – or turning their head in varying and unique directions. These mechanisms can (by nature) create barriers for individuals with disabilities, as the required actions may be difficult or impossible for some users to complete.
- A passive challenge-response process happens without requiring explicit user actions. Passive challenge-response mechanisms can ensure a high level of assurance without impeding inclusivity and accessibility. They provide the highest assurance that the user is not only ‘live’ but also authenticating in real-time – which is essential for defense against many sophisticated attack vectors.
Ultimately, not all biometric solutions are created equal. The key is intelligently mapping the appropriate level of liveness detection rigor to the risk profile of the use case, so organizations can strike the right balance between security and usability for their use cases.
Active challenge-response is not as secure as passive. When the security check is randomized, it’s tougher for bad actors to trick the system. Read more about how iProov ensures randomized passive challenge-response here.
Overall, organizations must consider the evolving threat landscape, the context of the user’s actions, and the specific activities being performed when determining the right identity verification approach. By striking the right balance between security and usability, businesses can enable convenient and trusted digital experiences for their users.
Choosing the Right Solution for Remote Identity Verification – Additional Considerations
In addition to mapping security levels to risk, organizations must also prioritize inclusivity and plan for a continuously evolving threat landscape when choosing a remote identity verification solution.
Throughout the webinar, both speakers emphasized the importance of balancing security and usability. As Jackson pointed out, “It’s not okay to simply continue to compromise usability as you increase security.” He advocated for inclusive and bias-free biometric systems that work for all users, regardless of age, gender, or demographic factors.
Palmer echoed this: “Everything must be considered in an evolving threat landscape. When considering the authentication mechanisms for your users, you need to consider what might be in the future, not just what is good enough today, because tomorrow the threat will have increased.”
If you’ve read this far and want to learn more about…
- Inclusivity, accessibility, and bias = read our “Ensuring Equitable and Inclusive Access” report here.
- The evolving threat landscape and what can be done to combat sophisticated attacks = read our “Threat Intelligence Report 2024: The Impact of Generative AI on Remote Identity Verification” here.
- Biometric face verification specifically and why we champion it over other biometric modalities = read our Demystifying Biometric Face Verification Report here.
Key Webinar Takeaways
- Remote identity assurance is not a binary choice. The appropriate security level depends on the risk and context of each use case.
- Balancing security and usability is crucial, as overly complex authentication processes can lead to user abandonment.
- Biometrics, particularly facial verification with challenge-response mechanisms, offer a high level of security for high-risk transactions.
- Continuous monitoring and adaptation are essential to keep up with evolving threats and maintain trust in digital identities.
As digital transformation accelerates, the insights from this webinar provide a valuable framework to help organizations navigate the spectrum of identity assurance needs. By intelligently mapping security levels to risk profiles while prioritizing usability and inclusivity, businesses can deliver secure yet seamless digital experiences that foster trust with their users.
