Creating Value for Users and Governments: How AI Can Enhance Digital-ID Solutions

Simple Identity Orchestration & Secure Face Verification On Any Device | iProov + Monokee
What Is KYC and Why Is It Important? How Is It Part of AML?
iProov’s Amlani Testifies at Homeland Security Hearing on AI

Breaking Barriers: Einat’s Journey With Visual Impairment in Cybersecurity

What Can Organizations Deploying Remote Identity Verification Learn From The iProov Threat Intelligence Report?

How Does iProov Secure Against Evolving and Yet Unknown Attacks?

What You Need to Know About Biometric Conformance And Testing

How Deepfakes Threaten Remote Identity Verification Systems

FIDO Reveals New Authentication Statistics | The Era of Biometric Face Verification

The Growing Importance of Biometric Identity Verification in Fighting Identity Theft and Fraud | ITRC Report

Unlocking The Future of Finance: Digital Transformation With Biometrics | UBS & KuppingerCole
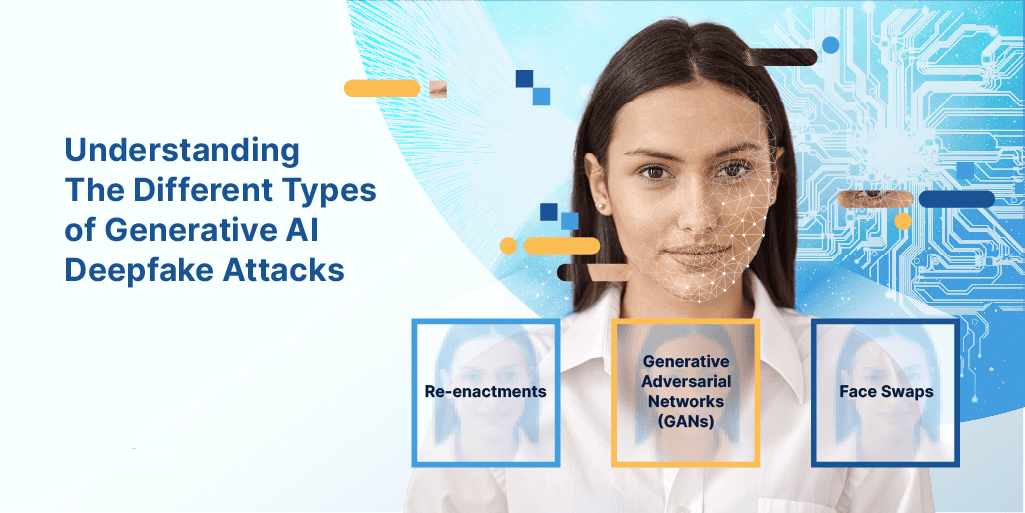
Understanding The Different Types of Generative AI Deepfake Attacks
Why Is Biometric Face Verification Ideal for Enrollment and Onboarding?
From Voice to Face: Transitioning Your Biometric Authentication
Spot The Deepfake Quiz
Put your deepfake detection skills to the test and see the types of synthetic media iProov defends against! Click Here.