May 10, 2024
In the digital era, ensuring secure remote identity verification and authentication is paramount for organizations. Inherence-based security factors have emerged as the most secure and trusted way of verifying users, but the rise of deepfakes and other synthetic media can make it difficult to ensure user legitimacy. The recent deepfake video conference phishing scam that cost a Hong Kong company more than $25m serves as a stark reminder of the AI-fueled threat landscape we must confront.
The rise of deepfakes and other AI-generated synthetic media poses a significant threat to remote identity verification. While various methods of verifying identity remotely exist, such as video call verification, face biometrics has proven to be the most secure, usable, and inclusive method. Others modalities, such as voice, have proven to be particularly susceptible to generative AI.
If remote identity verification security is to withstand the assault of generative AI capabilities, robust liveness detection coupled with active threat monitoring is critical to defend against evolving deepfake attacks. This is where facial biometrics with cloud-based architectures and dedicated security operations centers play a vital role.
iProov has been at the forefront of detecting, mitigating, and observing these evolving AI-based attacks for years. Through our cloud infrastructure and security operations center, we have unique visibility into the network and operations of malicious threat actors – and we are providing you with some of the intelligence gathered about their activities.
Why Is There No Comparable Report Available?
The remote identity verification threat landscape remains poorly understood relative to other cybersecurity domains, such as ransomware and phishing. While most biometric vendors track metrics like pass/fail rates, they cannot continuously observe live attack attempts because they do not deploy a cloud delivery model and a dedicated Security Operations Center.
On-premise biometric solutions have limited insight into their threat exposure, precluding them from gaining visibility into real-time threats against their systems as they occur. This inability to actively monitor attack attempts hinders their understanding of evolving threat vectors, patterns, and the groups behind them.
iProov’s cloud architecture, coupled with our iProov Security Operations Center (iSOC) – supported by a world-class science team of ethical hackers, threat intelligence agents, and biometric security experts – enables us to directly witness threat actors’ activities. This unmatched real-time visibility into the evolving threat landscape is why only iProov can produce this report.
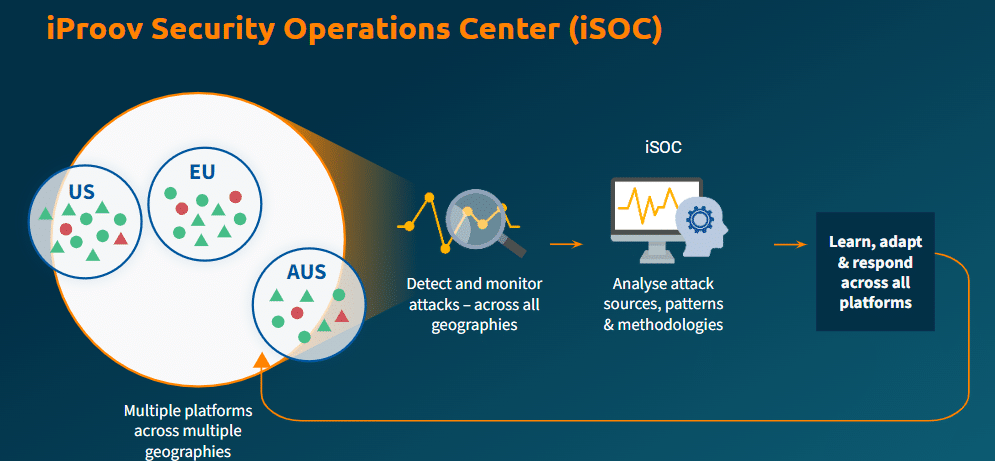
Given iProov’s unique visibility into the evolving remote identity verification threat landscape, this report provides invaluable insights that other vendors cannot offer. Here are the key reasons why organizations should read this report:
Why Read the Report?
1. Uncover The Latest Threats And Vulnerabilities
The Threat Intelligence Report serves as a comprehensive guide to the evolving threat landscape. Utilizing the findings of iProov’s science team, organizations gain exclusive insights into the tactics and tools employed by threat actors. We categorize them into a taxonomy of threats in the report.
Knowing about new threats and weaknesses allows organizations to proactively enhance their remote verification methods before criminals can exploit them. Staying ahead of criminals requires understanding the latest threats and vulnerabilities before they are targeted.
So, what does the taxonomy of threats look like?
- Presentation Attacks: An artifact is presented to the camera. iProov can detect presentation attacks via clues in the imagery. Presentation attacks are well understood and pose less of an evolving threat to remote identity verification; they are limited in scalability and globally recognized standards for Presentation Attack Detection (ISO/IEC 30107) exist.
- Digital Injection Attacks: Digital injection attacks involve injecting fake imagery directly into the video stream, enabling threat actors to bypass traditional presentation attack detection mechanisms and potentially launch large-scale, automated attacks. Standards and testing methods are still in development to counter this emerging threat.
- AI-Generated and Synthetic Attacks: AI-generated and synthetic attacks leverage advanced technologies like deepfakes, generative AI, and computer-generated imagery (CGI) to create fake or manipulated media that can impersonate individuals. They can allow large-scale, automated attacks.
The taxonomy of threats to remote identity verification:

This knowledge provides a clear framework for organizations to understand the threats against them. It empowers organizations to inform their cyber threat detection and prevention methods (and make informed decisions about the solutions they choose).
2. Deepen Your Understanding of AI-powered Tools
Generative AI has significantly impacted the field of remote identity verification. Not all technologies offer the same levels of assurance, making it crucial to gain a deep understanding of the proliferation and advancement of AI-powered tools and how they are being leveraged by threat actors.
The iProov Threat Intelligence Report sheds light on the vulnerability of person-to-person identity verification to deepfakes and their impact on remote verification. While basic liveness detection can defend against some attacks, iProov’s Dynamic Liveness serves as an effective solution against presentation, digital injection, synthetic identity, and AI-generated threats – ensuring the user is the correct and genuine person at the time of authentication.
Different technologies offer different levels of protection against these threats, and depending on the use case and risk, understanding the threat landscape helps organizations navigate through solution offerings based on risk appetite and the threats they require most protection from.
3. Gain Insights Into The Importance of Expert Insight in Identity Verification Processes
Efficient identity verification processes are a sensitive ecosystem. iProov manages this security through a feedback loop between our:
- Red team: conducting penetration testing
- Threat Intelligence team: conducting ongoing intelligence gathering
- Biometric Security team: covering real-time monitoring of fraudulent attempts
- Science team: Building and improving the platform based on feedback from above
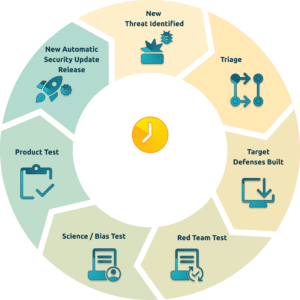
The report also touches upon the balance between human judgement and automation. The report offers valuable insights into this dynamic, helping organizations strike the right balance based on their specific needs and risk profiles.
4. Glimpse Into the Modus Operandi of Threat Actors
The report delves into the tactics, patterns, and tools employed by prolific threat actors over the years, providing a rare window into their methods and motives. This knowledge enables organizations to enhance their security measures, ensuring their defenses are prepared for novel and evolving threats.
This window into their MO shows that no tool is the same, and no method is the same either. So, it’s crucial to invest in vendors focused on tracking – in the words of Gartner – the “latest available tools and techniques for creating deepfakes” to maintain the “most up-to-date perspective on potential attacker capabilities and your ability to detect them.”
5. Gather Key Statistics on the Threat Landscape
The report uncovers key statistics on threats to remote identity verification – such as a shocking 704% increase in face swap (a form of deepfake) attacks from H1 to H2 2023 – that can help guide your understanding of attack trends and risk qualifications.
Understanding the severity of the risk with empirical data points can guide organizations’ decisions about technology adoption and risk mitigation strategies.
- Those looking for more information about evaluating biometric face verification solutions should refer to our Demystifying Face Verification Report.
Why Should You Care?
Identity verification threat intelligence is crucial for any organization relying on digital identities to ensure users are truly who they claim to be. The rapidly evolving landscape of AI-powered attacks threatens all remote verification systems, including those without biometrics like video conferencing. It’s not a matter of if, but when your organization will be targeted.
Choosing the right remote identity verification vendor with cutting-edge solutions to combat emerging threats is critical. iProov is at the forefront of biometric security, with iSOC continuously monitoring fraud techniques to adapt our technology preemptively. Our 2024 Threat Intelligence Report provides exclusive insights from our Science team on the evolving tools and methods used by threat actors, empowering organizations to assess whether iProov’s approach aligns with their security needs for defending against AI-powered identity threats.
In an era of generative AI, not all verification technologies offer equal protection. By leveraging the insights from this report, organizations can make informed decisions about the solutions they deploy to defend against growing threats.
Closing Thoughts
There is a need for a security mindset overhaul within the field of remote identity verification – a reactive, after-the-fact security posture is insufficient. In truth, vendors without visibility into their attack surface are not a long-term secure solution.
Organizations need a proactive security mindset with real-time insight into emerging threats to properly assess and mitigate risks when selecting a remote identity verification solution.
Ultimately, by leveraging the insights from this report, organizations can make informed decisions about the solutions they deploy to defend against growing threats. To access the iProov 2024 Threat Intelligence Report and learn more, visit https://www.iproov.com/reports/iproov-threat-intelligence-report-2024



