May 9, 2025
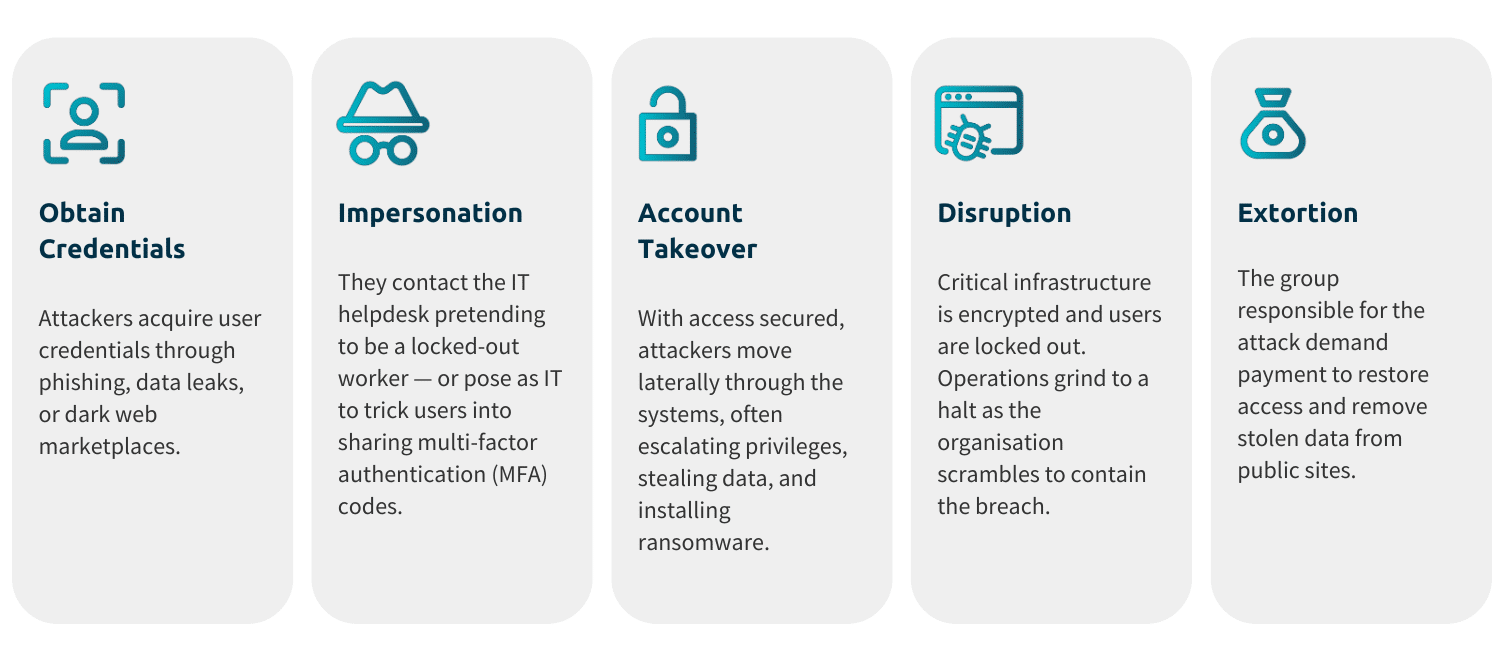
The recent ransomware attacks on M&S, Co-op, and Harrods reveal a familiar pattern: attackers no longer rely on hacking company networks — they often log in via the helpdesk. As identified by Gartner, account recovery due to forgotten passwords or lost credentials is the riskiest part of the identity management life cycle. Just like the MGM Resorts breach in 2023, which led to $100 million in losses, these incidents show how vulnerable account recovery processes are to social engineering attacks.
The Anatomy of a Social Engineering Attack
How AI Makes Social Engineering Attacks Easier
AI is turning cybercrime into a low-skill, high-scale operation — automating phishing, developing deepfakes, and enabling malware that adapts faster than defences can respond. These technologies not only reduce the effort required by attackers but also significantly increase their speed, accuracy, and reach.
- Target Identification: AI-powered tools scrape and analyze large volumes of public data — from LinkedIn profiles to breached databases — to build detailed target profiles. Natural language processing helps identify job roles, relationships, and communication patterns to create highly believable phishing lures or impersonation attempts.
- Credential Stuffing: AI accelerates brute-force login attempts by prioritizing commonly reused passwords and adjusting strategies in real time. In 2024, Microsoft reported 7,000 password attacks per second. Research has shown that AI can crack over 50% of weak passwords in under a minute.
- Impersonation: Deep learning models are used to create realistic deepfake audio and video, mimicking voices and facial movements with high accuracy. This enables attackers to convincingly impersonate workers in live support calls, video meetings, or even voicemail messages.
- MFA Fatigue Attacks: AI scripts manage repeated push notification attempts, timing them during likely moments of distraction (e.g., lunch breaks or end of day). Some attackers even combine this with voice deepfakes posing as IT support, urging users to accept the prompt.
These AI-enhanced methods are proving effective. In 2024, 42% of organizations reported successful phishing, vishing, deepfake, or other social engineering attacks (Global Cybersecurity Outlook 2025, World Economic Forum).
The Core Problem: Shared Secrets Will Always Be Shared
As AI accelerates the capabilities of threat actors, organizational authentication is still predicated on weak knowledge and possession-based methods, passwords, SMS codes and authenticator apps. These shareable credentials are easily coaxed out of victims and shared over the phone.
The root issue is trusting what someone knows or says, instead of verifying who they are. The workforce has changed faster than most security architectures. Remote access, BYOD, and cloud-first environments have made traditional, perimeter-based authentication obsolete.
The UK’s National Cyber Security Centre (NCSC) has urged organizations to reassess how IT helpdesks authenticate users — particularly when handling privileged accounts. While cybersecurity experts are advocating for more layers of security to prevent future attacks, such as code words shared with the help desk, if these layers consist of shareable secrets, they’re vulnerable.
Face Biometrics Are Phishing Resistant
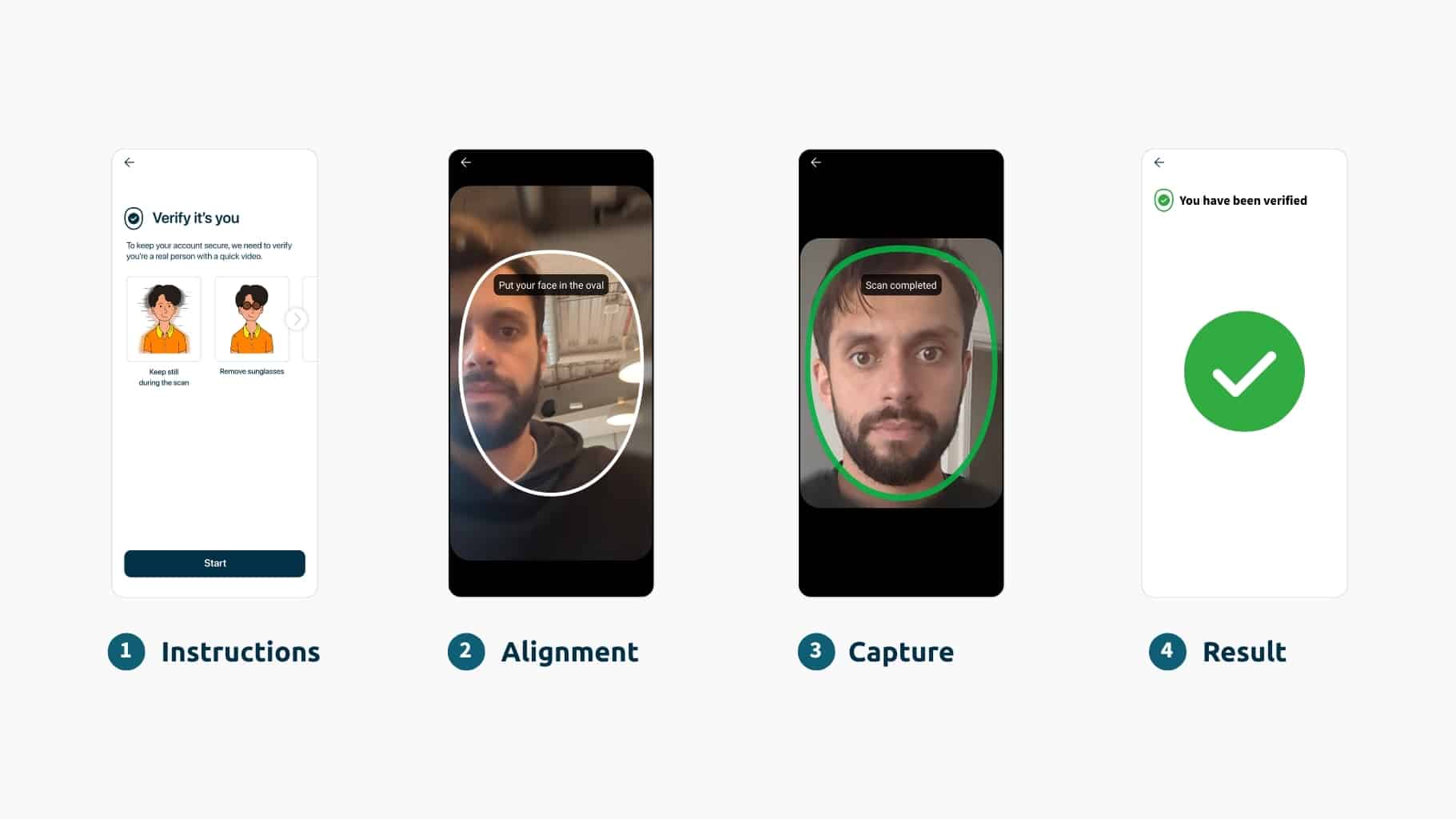
Facial biometrics with liveness detection offer a fundamental shift in workforce verification and authentication.
- It’s not a secret — your face can’t be shared or phished.
- It confirms identity — not just whether you know a code or can access a device, but who you are.
- It verifies genuine presence — a critical capability in today’s remote world.
Even if an attacker convinces someone to authenticate, they’ll only get a selfie. Strong cloud-based liveness detection ensures that images and videos — even high-quality fakes — can’t be used to bypass authentication workflows, and is always evolving to mitigate new AI-based attacks.
Face biometrics is the only way to connect user activities to the real, live human. As organizations strive to go passwordless and implement Zero Trust architectures, this is a critical capability to reduce risk and keep the workforce secure.
Secure Your Account Recovery Process
As AI accelerates the scale and sophistication of social engineering, the need for high-assurance, phishing-resistant authentication has never been clearer. Face biometrics with liveness detection offers a secure way to verify identity — not just credentials — at the point of highest risk.
If your organization is re-evaluating how users are verified during support calls, especially for privileged access, this is the time to act.
Don’t let your helpdesk become your weakest link. Talk to us today about deploying biometric authentication that resists social engineering attacks, MFA bombing, and sophisticated deepfakes.