June 2, 2023
Mela Abesamis had always considered herself careful when it came to cybersecurity. She was well aware of phishing attacks and other common fraud tactics, and how to spot them. She was also used to receiving One-Time Passcodes (OTPs) from her bank, sent by SMS to her mobile device to authenticate her identity.
But then in December 2020, Mela received a message from her bank, saying that 50,025 Philippine pesos (around $950) had been moved from her account to a Mark Nagoyo. This was the first and only indication she received that money had been transferred. She had never heard of Mark Nagoyo, she certainly hadn’t made the payment, and she had not received a one-time passcode during the transaction.
She wasn’t alone. Over 700 account holders were affected by the fraud. In Filipino, the word “nagoyo” means to make a fool out of someone.
Four individuals were eventually indicted for the scam. The fraudsters had used a combination of social engineering and phishing techniques to harvest the bank log-in details and cellphone numbers of hundreds of citizens. With these, they could intercept SMS OTPs and drain people’s bank accounts.
The bank repaid the affected amounts, but this didn’t fully offset the traumatic experience for the victims.
OTP Authentication: What’s The Issue?
This is just one example of how compromising OTP authentication is becoming less and less of a challenge for increasingly sophisticated hackers. It would seem that OTP authentication is no longer fit for purpose as a security method. Yet, they remain a common verification process for organizations across the globe.
This article looks at the security risks that come with OTP authentication. It discusses how hackers are able to compromise the process, and proposes safer and more accessible alternatives for identity verification.
What Is OTP Authentication?
If you’ve ever used online banking, chances are you’ve completed an OTP authentication.
An OTP (One-Time Passcode) is a computer-generated code delivered via email, Short Message Service (SMS), or hardware token. The code serves as a form of authentication or verification that you are who you say you are because you’re in possession of your device.
You then enter the code from your SMS into the online field in order to gain access to a given website or app. The code will expire in a limited time.
OTP authentication is often used as a method of multi-factor authentication (MFA) and meets the what you have factor of assurance.
Multi-factor authentication requires two or more of the following elements:
- Knowledge: something only the user knows – eg, a password or PIN
- Possession: something only the user possesses – eg, a mobile handset or token
- Inherence: something the user is – eg, a biometric
The two factors also need to be independent of each other. The objective is to make it more difficult for an authorized person to access an account through layered security.
In the case of OTPs, the ‘what you have’ is your mobile device.
The Main Types Of OTP Authentication:
- SMS OTP authentication: A one-time passcode is sent to your mobile device via text message.
- TOTP (Time-Based One-Time Passcode): You are instructed to open an authenticator app where you’ll find a passcode. You are given 30-60 seconds to enter the passcode into the website, app, or portal you are trying to access before it expires.
- Hardware tokens: A physical device (not a cellphone) displays a one-time passcode that enables you to access a website, app or portal.
What Are The Security Risks Of OTP Authentication?
The fundamental issue with OTP authentication is that it only meets the what you have factor of authentication (otherwise known as the possession factor). What you have – be it your cellphone or hardware token – can be lost, stolen, or compromised.
SMS OTP authentication security risks
As shown in the case in the Philippines, hackers don’t need to steal your cellphone to compromise SMS OTP authentication. In fact, they don’t have to be anywhere near you.
Text messages aren’t encrypted, and they’re tied to your phone number rather than a specific device. Below are two types of common attacks that enable hackers to intercept SMS OTP authentication:
- SIM swaps. The fraudster harvests personal details from the victim, either via phishing or social engineering. They use these details to convince the phone provider to switch the number to their device. The SMS OTP is then sent to the attacker, allowing them to verify and complete the activity.
- The SS7 flaw. SS7 (Signaling System No. 7) is a protocol that facilitates all mobile phone activity, including SMS messages. The trouble is that it includes a design flaw that means hackers can intercept calls and SMS messages.
When a mobile network provider’s SS7 protocol is successfully compromised, attackers have access to a wealth of users’ personal data. Crucially, they can intercept SMS messages and phone calls.
Not only does this allow attackers to authenticate fraudulent activity using OTPs, but it allows them to do it at scale.
In Germany in 2017, fraudsters compromised the 02 Telefonica SS7 protocol and intercepted SMS OTPs. It led to an undisclosed number of bank account holders having funds removed from their accounts.
TOTP Authentication Security Risks
TOTP and app-based authentication offer more security than their SMS counterpart. The fact that the OTP is constantly changing and is not linked to your phone number makes it harder for attackers to compromise.
That said, TOTP authentication isn’t entirely without its flaws. For example:
- Device vulnerability. TOTP authentication still only meets the what you have factor of authentication. No matter how encrypted the OTP, the reality is that your device can be at risk. Mobile devices can be lost or stolen.
This brings into question whether OTP authentication can actually be classified as MFA. If an attacker steals your cell phone, carries out an activity (such as making an online payment), and then uses your TOTP authenticator app to authorize it – can we really say they used multiple factors? After all, it all happened on the same device.
On the other hand, iProov face authentication is out of band – a type of authentication method that utilizes a separate communication channel, or ‘band’. iProov technology assumes that the device has been compromised and so the authentication is processed securely and privately in the cloud. An iProov authentication is therefore independent of the device being used. Even if a bad actor had full access to another’s device, the authentication process remains secure.
Does OTP Authentication Offer An Outdated User Experience?
The global pandemic forced many people to carry out their daily activities remotely. This led to surging demand for quick, effortless, and inclusive user experiences.
However, the experience that OTP authentication provides comes with its shortfalls. We’ll discuss them here.
Active process
An active process in this sense means that the user has to do something for the activity to work. Regarding OTP authentication, it means retrieving your phone or hard token.
This can be irritating. You may not have your device with you at all times. Therefore, you’re required to fetch it to complete the activity, adding friction to the user experience.
This is especially the case for TOTP. The time-sensitive nature of this verification process can result in the one-time passcode expiring before you’re able to use it. Oftentimes, users become so exasperated by the procedure that they abandon the whole activity.
Reliance on phone signal
OTP authentication relies on the assumption that you have a phone signal or access to the internet. If not, it doesn’t work. With SMS OTP, not having a strong signal can delay the passcode, meaning that you have to wait to complete the activity.
Let’s say you’re trying to buy airline tickets urgently, or you have a family member who’s genuinely in a predicament and needs money. You begin the transaction online, and the SMS OTP is sent to you, but you have no phone signal.
You don’t receive the OTP and have no other way of making the purchase or transferring the funds to help your family member.
A lack of inclusivity
Lastly, OTP authentication wrongly assumes that everybody has access to a mobile device. Not everybody does. The global pandemic forced everybody – cell phone owners or not – to carry out access services remotely.
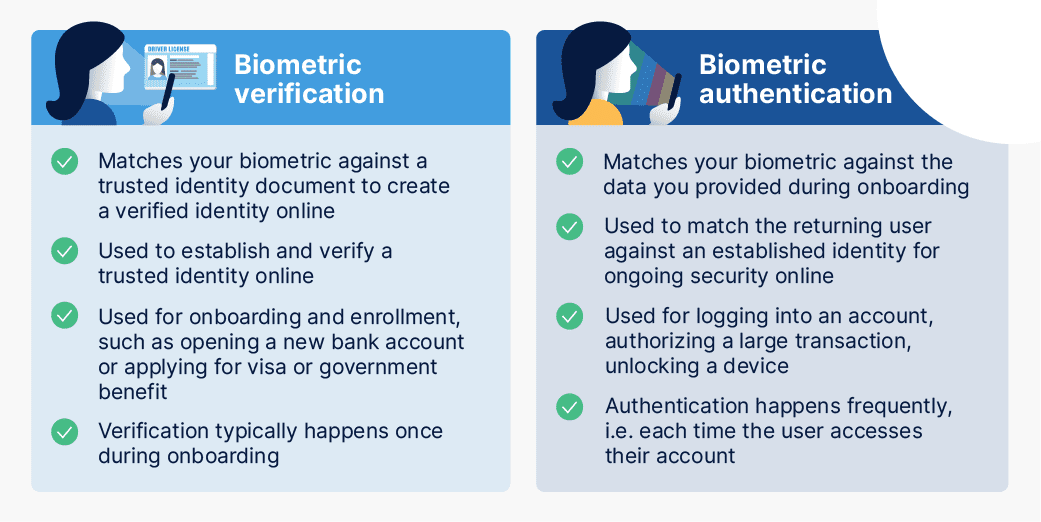
Why Is Biometric Verification A Better Alternative To OTP Authentication?
Whereas OTP authentication meets the what you have factor of authentication, biometric verification employs what you are verification. That means it uses your inherent characteristics, such as your face, to verify your identity.
While a one-time passcode can be lost or stolen, nobody can steal your face. As such, biometric authentication can offer a more secure method for organizations to verify users against a government-issued ID (which generally use photos of the face) to validate them during onboarding and enrollment.
How Does Liveness Weigh Up Against OTP Authentication?
As stated previously, your inherent characteristics, like your face, can’t be stolen. But they can be copied. Attackers can present a mask, picture, or recording of the victim to the camera to spoof the authentication process.
This is where liveness comes in. Liveness detection uses biometric technology to verify that an online user is a real live person. OTP authentication cannot deliver such levels of assurance. Mark Nagayo was not a real person, but the scammers were able to verify hundreds of transactions using stolen credentials.
How is Biometric Face Verification Different From OTP Authentication?
Liveness detection uses facial verification to assure that it’s the right person and a real person – two layers of security that OTP authentication cannot achieve.
However, liveness detection can’t verify whether a person is verifying right now. iProov’s science based biometric solutions, on the other hand, can. It does this with iProov’s Flashmark™ technology, which illuminates the remote user’s face with a unique, randomized sequence of colors that cannot be replayed or manipulated synthetically, preventing spoofing.
Unlike SMS OTP authentication – which uses compromisable phone networks to deliver passcodes – iProov is a cloud-based technology, meaning its defenses are hidden from attackers, making it much harder for attackers to intercept vital data.
As discussed, OTP authentication falls short of providing an effortless user experience, largely because it forces users into an active process. GPA, meanwhile, is entirely passive. Using any device with a front-facing camera (a cell phone, a laptop, a kiosk), users simply need to look at the camera and the authentication will be done for them. The authentication works irrespective of cognitive ability because there are no complex instructions to read, understand, or execute.
If you want to make your online customer onboarding or authentication more secure and effortless and want to benefit from biometric authentication, request a demo here.