September 7, 2023
A wide variety of methods are available to authenticate users remotely, ranging from passwords and one-time passcodes (OTPs) to fingerprint scanning and face authentication.
Each relies on a different factor to establish trust:
- Something you know (like passwords)
- Something you have (using your phone for OTPs)
- Something you are (biometrics, such as your face).
In recent years organizations have started to move away from knowledge-based authentication. Passwords are not secure, because they can be shared, guessed or stolen. Passwords also cause user frustration, because they are easily forgotten. This ultimately leads to drop-off and poor completion rates. You can read more about the end of passwords here.
Instead, organizations are moving toward passwordless solutions. Biometric forms of authentication use something you are to prove your identity. These are convenient—you always have your face with you, for example—and while they can be copied (using a photo), they cannot be stolen. And in the case of iProov’s Dynamic Liveness, biometric authentication technology can deliver the highest levels of security and inclusivity.
Why Do We Need Authentication?
Authentication is needed to securely identify your online users. It’s most commonly used when logging into an account or authorizing a financial transaction remotely, for example. Ultimately, authentication is needed to restrict and allow access to personal information and accounts. As the demand for remote services grows, and cybercrime increases, so does the demand for secure authentication online.
Secure user authentication…
- Protects your customers from the emotional and financial impact of identity theft
- Defends your organization against financial loss through fraud and other crime
- Reduces the risk of your organization being used for money laundering
- Helps to ensure that your organization is complying with regulations, such as Know Your Customer (KYC)
- Ensures your organization is reassuring its users and protecting its reputation
But which authentication method is the right or “best” authentication method for you?
How Can You Choose the Right Authentication Method?
For your users, the best authentication method will be something that offers convenience, speed, and reassurance. For your organization, the best solution will deliver the appropriate level of security, high completion rates, and will be inclusive to the largest number of customers or citizens.
The things you need to consider include:
- Security: If the risk profile of the transaction is high, you’ll need a more secure method of authentication. For example, an activity with high financial value (like moving funds from a bank account, or accessing a pension fund or government benefits) will require the highest level of authentication security.
- Usability: If authentication is overly complex, people find workarounds—for example, when passwords require multiple special characters, people tend to write them down, which makes them less secure and user-friendly. Consider who your service is aimed at but remember to be inclusive. Most online services need to offer maximum inclusivity, so simplicity and effortlessness are always the aim.
- Convenience: Customers value convenience, and some authentication methods are better than others in this regard. For example, a customer making a payment on their desktop computer who then needs to fetch their mobile device for an OTP will likely experience frustration.
- Reassurance: It’s possible to make things too easy. If a customer is making a large payment and doesn’t experience any sort of security authentication, they may be unnerved, which could cause them to distrust your company.
- Completion rates: If your authentication process asks the user to follow too many instructions, or if it takes too long, or it needs repeated attempts before it succeeds, there’s a high risk of drop-offs and lost business. This impacts any organization, whether it’s a retailer dealing with abandoned baskets or citizens failing to return to access online government services.
- Privacy: The best authentication method should not compromise a user’s privacy. For instance, a commuter on a train wanting to complete a transaction on their mobile device may not appreciate needing to speak out loud with voice recognition.
The Five Most Popular Methods of Online Authentication
Next, we’ll review some of the most popular authentication methods that organizations employ to secure their systems.
1. Face authentication
Facial authentication uses a face scan done by a human on any device with a front-facing camera to prove they are who they say they are. For face authentication to be secure, it needs to verify that the user is the right person, a real person, and that they are authenticating right now. This is what iProov’s Dynamic Liveness technology delivers.
Some other forms of face authentication use single images to match a physical face to a trusted image, but they can be spoofed by “presentation attacks”, including photographs shown to the device’s camera. iProov technologies use multiple frames to securely determine the authenticity of an individual.
Facial authentication has many advantages over other biometric methods. One is that everyone has a face, and most government-issued ID documents have a photo but don’t include fingerprint or other biometric data. This means that a user could scan their identity document using their mobile device and then scan their face to prove that they are who they claim to be—completing an entire verification process all from the comfort of their couch.
Face authentication can also be done on general-purpose hardware. Any smartphone or computer or other devices with a user-facing camera can support face authentication, while fingerprint or iris scans need specialist hardware.
This transforms the way that governments and enterprises can securely verify the identity of online users. Citizens can apply for bank accounts, credit cards, healthcare, tax, or any other secure service without needing to visit a physical building for an identity check.
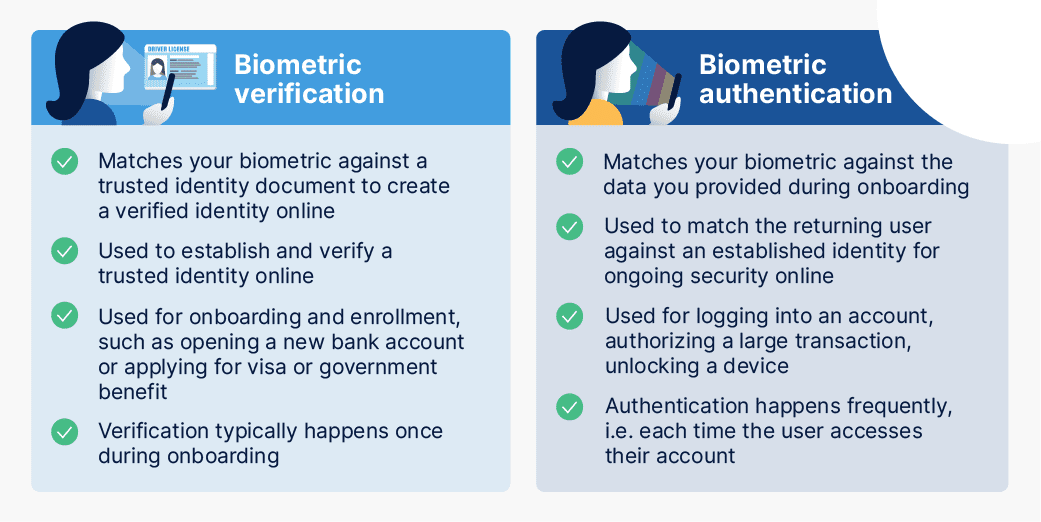
Face authentication and verification are sometimes referred to as “face recognition”—but these are completely different technologies. Learn the difference between verification and recognition here.
2. Fingerprint scanning
Fingerprint authentication compares a user’s fingerprint to a stored template to validate a user’s identity. Fingerprints are complex and unique, which makes them impossible to guess. They are also convenient to use on a smartphone or other device that has the capability to read a fingerprint.
There are limitations to fingerprint authentication. Firstly, because not everyone has a fingerprint scanner on their device, fingerprint authentication is not an accessible and inclusive method for all. It’s a method limited to those who own more expensive devices.
And, just like passwords, there are security concerns. Fingerprints can be copied using silicon rubber, plus they can be hacked on most devices in around 20 minutes. Fingerprint authentication can be good for low-risk scenarios where quick access is needed but it lacks the accessibility of other methods such as face authentication.
3. Voice authentication
Voice authentication measures the physical and behavioral markers in a user’s speech to confirm their identity. Using all the information in human speech enables an effective means of authentication that works on a phone or video call.
Voice has become a popular form of verification with financial institutions but is prone to background noise, can be overheard, and can be spoofed by a recording or deepfake.
4. SMS One-Time Passcodes
SMS One-Time Passcodes (OTPs) are unique, time-based codes that are sent to the phone number tied to a user’s account. OTPs prove possession of a device/SIM—something you have—because only one person should have access to their SIM and text messages.
There are a number of issues with this form of authentication.
- SMS codes can add complexity and additional steps to the authentication process. If customers are using a computer to complete a task online and are asked to find their mobile device to retrieve an SMS code, it can be frustrating and potentially cause the user to drop off and abandon the transaction.
- SMS codes are not secure – they can be hacked and diverted. Devices are also often lost, stolen, and shared. OTPs are only as secure as the device they are sent to.
- SMS codes are in-band authentication, which offers less security than you might expect. If a user is buying something via a mobile app and the app provider sends an SMS code to that mobile device to verify the purchase, the SMS code is not actually providing any additional security—the code is being sent to the same device and is, therefore ‘in-band’. If the device has been compromised, the OTP is worthless. iProov face authentication is out of band: it assumes that the device has been compromised and so the authentication is processed securely and privately in the cloud. An iProov authentication is therefore independent of the device being used. Even if a bad actor had full access to another’s device, the authentication process remains secure.
5: Passwords
Passwords are ubiquitous, and the authentication method we’re most familiar with. But they’re not secure. They’re often forgotten, stolen, lost, or shared—as we highlighted in our flagship report, The End of Password. Plus, our research has found that consumers are growing increasingly frustrated with passwords, causing them to abandon their baskets when they forget them.
Passwords, and knowledge-based authentication in general, suffers a fatal flaw: the more secure you make it, the less accessible it is for users. The passwords that fraudsters cannot guess or hack are also harder for people to remember. And as we create more and more accounts, it becomes harder and harder to remember them all. Other threat vectors such as brute force attacks and credential stuffing are a big concern too.
Our previous research also found that over 50% of users have abandoned purchases because they forget their password and retrieving it took too long, so there’s a clear commercial penalty here.
This ubiquity makes passwords the common choice for authentication. But the truth is that passwords are better used in conjunction with other more secure and effortless methods of authentication, such as face authentication. These applications include multi-factor authentication and step-up authentication. However, one strong authentication is better than two weak ones.
iProov Uses Face Biometrics for Authenticating Users Securely and Inclusively
Here at iProov, we provide biometric face verification to some of the world’s most secure organizations to enable them to authenticate online users.
Consumers prefer methods that do not add additional complexity or effort to their services, transactions, and accounts. So, we eliminated the complexity—while still retaining national-grade security. This enables you to onboard and authenticate customers and users, with the minimal number of steps for users.
iProov’s biometric authentication provides:
- Genuine presence assurance: To deliver secure biometric face authentication, you must be able to establish that an online user is the right person, a real person, and that they are authenticating right now. Genuine presence assurance detects digital injected attacks, as well as artifact and imposter attacks.
- Cloud-based authentication: Cloud-hosted authentication solutions do not rely on the user’s device for security and are less susceptible to biometric security compromise. Cloud-based authentication also enables continuous active threat monitoring to constantly evaluate and respond to evolving attacks.
- Device and platform-agnostic capability: Users should be able to seamlessly authenticate themselves on any device without the need for specific hardware or devices.
- Effortless user experience: Authenticating with iProov is as simple as staring at your user-facing camera. Users do not need to read or follow instructions, or swap devices, and the user interface is inclusive and accessible.
And that’s why some of the world’s most security-conscious organizations, including…
- The UK’s Home Office
…choose iProov to verify, authenticate, and onboard their users.
Summary of the Best Authentication Methods
- The need for organizations to implement secure online authentication of remote users is growing, as cybercrime is increasing and regulations are changing
- There are many authentication methods available that offer different approaches within three categories: something you know, something you have, something you are
- It’s important to consider which authentication method suits your use case, taking security, usability, convenience, reassurance, completion rates, and privacy into consideration.
- Face authentication offers many benefits over other methods. A face scan can be verified against a trusted document, making it possible to securely validate the identity of the user. iProov’s facial biometric technology in particular is very inclusive as it can be completed on any device with a user-facing camera.
- iProov’s Dynamic Liveness technology delivers face authentication with the highest levels of security, convenience, privacy, and inclusivity.
If you’d like to see the benefits of using face authentication to secure and streamline user authentication for your organization, book your demo here. You can read up further on our customers and case studies here.