July 22, 2025
Native virtual cameras represent a critical breakthrough in identity fraud – they bypass traditional security measures by operating within standard device permissions, making them virtually undetectable by conventional cybersecurity systems. These sophisticated yet easily accessible tools intercept the device’s camera feed and seamlessly inject deepfakes or synthetic content, appearing as legitimate video streams to identity verification systems.
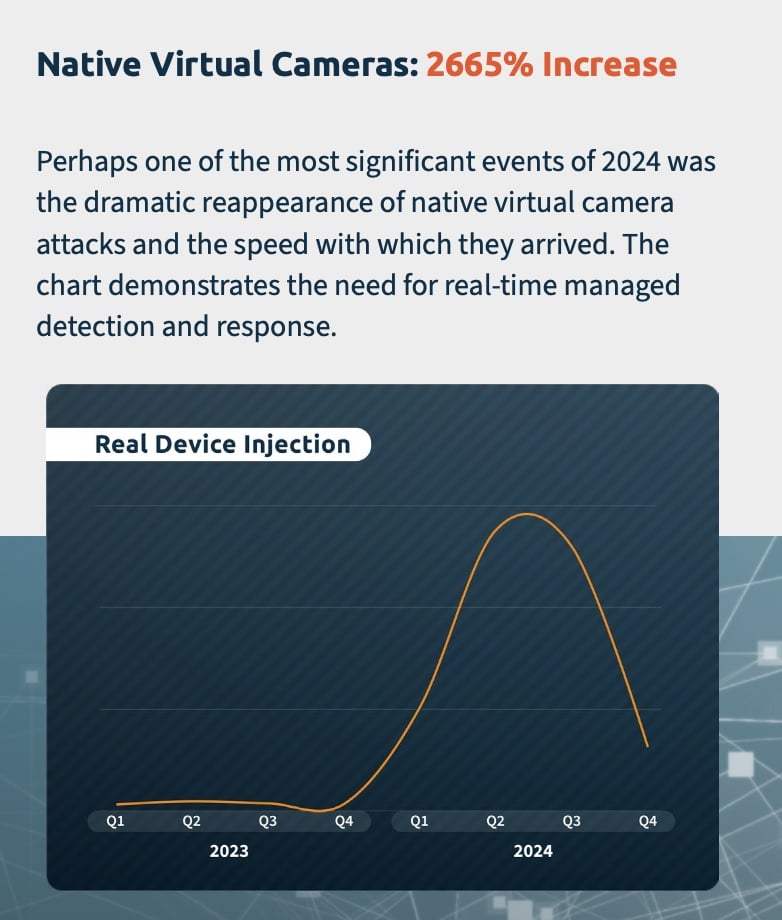
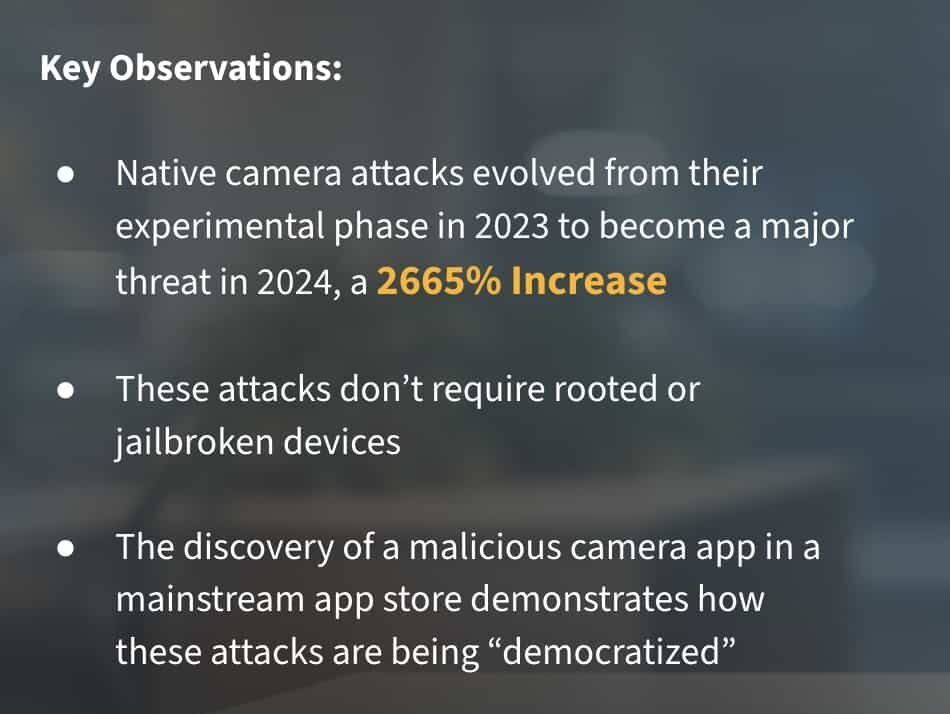
This invisible threat exploded by 2,665% in 2024, transforming from experimental techniques to one of the most dangerous challenges facing remote identity verification worldwide. As revealed in iProov’s 2025 Threat Intelligence Report, what once required significant technical expertise and modified devices can now be accomplished by anyone who downloads an app, including ones available on mainstream app stores.
What Are Native Virtual Cameras?
Native virtual cameras are software applications that run directly on smartphones and intercept video streams at the device level. Unlike earlier injection methods that required specialized hardware or rooted devices, these modern attacks operate within standard app permissions – the same permissions you’d grant to any camera or video app.
This evolution represents a fundamental shift in the threat landscape. The technology has evolved from requiring sophisticated technical knowledge to being accessible to anyone, democratizing advanced identity fraud techniques in an unprecedented manner.
The Alarming Rise: From Experimental to Mainstream
Our Security Operations Center (iSOC) data shows a clear progression in native camera attack evolution:
- Experimental Phase (2023): Limited probing attempts with basic capabilities
- Innovation Surge (February 2024): Significant increase following advancements in virtual camera tools
- Peak Activity (Q2 2024): 785 weekly attack incidents detected
- Tactical Shift (Late 2024): Reduced but more targeted attacks as threat actors became selective in their targeting
What makes this progression particularly concerning is that it reflects the broader success and maturation of native virtual camera tactics across the threat landscape. This isn’t merely a technological advancement – it represents a fundamental shift where threat actors have moved beyond experimental probing to developing sophisticated, proven methodologies. Having demonstrated the effectiveness of these attacks, criminals have become increasingly strategic in their deployment, systematically targeting organizations with vulnerable identity verification systems while sharing intelligence about successful breach techniques across global networks. Crime-as-a-service is developing alongside these methodologies as criminals share and sell their techniques.
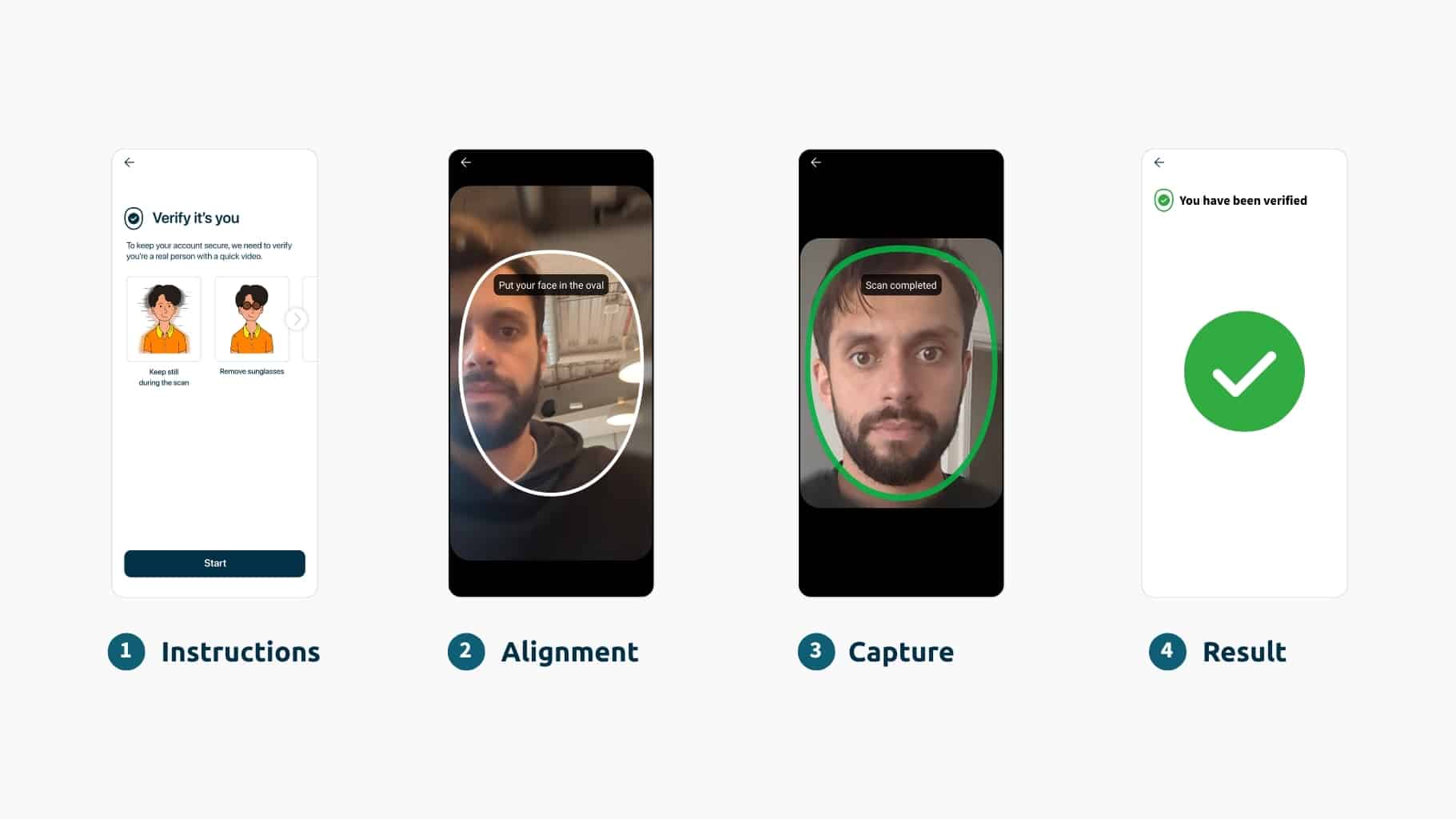
How Native Virtual Cameras Trick the Operating System
Understanding how these attacks work reveals why they’re so difficult to detect and prevent. The sophistication lies not in complex hacking, but in exploiting the normal way devices handle camera permissions:
- Legitimate Permission Request: The malicious application requests standard camera permissions identical to those used by legitimate video apps, such as Zoom or Instagram. As our intelligence team discovered, malicious apps are even found on legitimate app stores. The operating system sees nothing suspicious, so it doesn’t raise any alarms.
- System-Level Interception Once granted access, the app positions itself between the device’s physical camera and any application requesting video. This happens at the operating system level, making the interception completely invisible.
- Content Substitution Instead of passing through the real camera feed, the app injects synthetic content — deepfakes, pre-recorded videos, or manipulated imagery. The target application receives what appears to be a genuine camera stream with authentic metadata and device characteristics.
- Seamless Delivery The identity verification system receives the fraudulent video stream exactly as if it came directly from the device’s camera, with no indication that manipulation has occurred.
Why Traditional Security Measures Fail
The sophistication of native virtual camera attacks poses significant challenges for conventional security approaches:
- Legitimate Permission Structure: These attacks operate within standard device permissions, making them difficult to identify through permission monitoring.
- Intact Metadata: Unlike earlier injection methods, native camera attacks maintain proper metadata and device characteristics, bypassing many traditional verification checks.
- No Root Required: The most concerning finding in our 2024 research was that these attacks don’t require rooted or jailbroken devices, making traditional root detection insufficient as a security measure (rooting (or jailbreaking on iOS) is the process of gaining full administrative control over a device’s operating system, often to bypass restrictions or install unauthorized apps).
- App Store Distribution: Our researchers discovered malicious camera applications in everyday app stores, highlighting how these tools have moved from the dark web into seemingly legitimate distribution channels.
The App Store Problem
The discovery of a malicious camera application in a mainstream app store marks a significant milestone in the evolution of these attacks. Though the app was eventually removed from the official store after detection, it remains available through third-party sources, illustrating the persistent nature of these threats.
This development has profound implications for security strategies. App store presence provides these tools with a veneer of legitimacy and dramatically increases their potential distribution, scalability, and reach.
Beyond Biometrics: A Cybersecurity Challenge
The rise of native camera attacks challenges the traditional categorization of identity verification threats. These attacks exist at the intersection of biometric security and cybersecurity, requiring integrated defense strategies that address both domains.
Evidence from our threat intelligence clearly shows that robust defense requires both strong biometric liveness detection and cybersecurity measures working in concert. The attack patterns we observed suggest threat actors are actively exploring this dual-pronged approach, targeting weaknesses where these two security domains meet.
The Solution: How Can You Defend Against Native Virtual Camera Attacks?
Effective protection against these sophisticated attacks requires a multi-layered approach. It all starts with visibility; you can’t defend against what you can’t detect. The ability to identify suspicious activity in real time is the foundation of any effective biometric defense.
1. Real-Time Managed Detection and Response
Perhaps most critically, organizations need continuous monitoring capabilities that can identify novel attack patterns in real-time. The rapid evolution of these threats means static defenses quickly become obsolete. Security measures that can’t adapt quickly fall behind the threat, allowing new attack types to slip through unnoticed. That’s why managed detection and response, with real-time signals, is essential to keeping identity verification systems resilient.
2. Dynamic Liveness Detection
Traditional active liveness detection (based on challenge-response mechanisms like blinking or turning) is vulnerable to native camera attacks because it relies on predictable user actions that can be replicated. When these systems expect specific responses like blinking or head movements, virtual camera software can deliver synthetic imagery mirroring those behaviors.
The widespread use of active liveness detection has driven demand for native virtual camera attack tools, since they’re specifically designed to deliver the precise movements these systems require. Passive liveness detection solutions, such as Dynamic Liveness, avoid this vulnerability by not providing attackers with a predictable template of behaviors to replicate.
iProov’s Flashmark™ illuminates a unique sequence of light on the screen that is different every time. If that exact sequence is of reflections is not validated, we know it’s not a real person in real time.
3. Device Integrity Verification
While root detection alone is no longer sufficient, comprehensive device integrity checks remain an important defense layer. These should examine the entire video processing pipeline rather than just the device’s root status.
The Future of Native Camera Threats
The trajectory of native virtual camera attacks suggests continued evolution and increasing sophistication. As legitimate camera and video processing technologies advance, we can expect parallel developments in attack capabilities.
Particularly concerning is the potential integration of these attacks with other emerging threats, such as the image-to-video conversion techniques identified in late 2024. These combined attack chains could create extraordinarily difficult challenges for identity verification systems.
Native Camera Threat: Summary
Native virtual camera attacks represent a fundamental shift in the identity verification threat landscape. Their dramatic rise underscores the urgent need for organizations to re-evaluate their security strategies and implement multi-layered defenses capable of addressing this evolving threat.
The future of identity security lies not in any single technology but in comprehensive approaches that integrate biometric security, cybersecurity, and real-time threat intelligence. As these attacks continue to evolve, organizations must remain vigilant and adaptive, implementing security measures that can evolve as quickly as the threats themselves.
For a comprehensive analysis of native virtual camera attacks and detailed guidance on protecting your organization, download iProov’s complete 2025 Threat Intelligence Report.
Book a demo with iProov today to learn how our dynamic liveness detection technology can help protect your organization against native virtual camera attacks.