July 30, 2025
An employee logs in from London and is prompted to enter a one-time passcode (OTP).
Ten minutes later, the same user logs in from Sydney and enters another OTP.
Both attempts pass multi-factor authentication (MFA). Only one is legitimate.
This is the core weakness in many risk-based authentication (RBA) strategies: you’re triggering additional authentication, but not truly verifying who’s behind the screen.
Attackers know this – and they’re exploiting it.
Groups like Scattered Spider have compromised major organizations, including M&S, Co-op, and Qantas, by tricking users into approving fraudulent access. Armed with AI, they’re launching more convincing phishing campaigns, voice clones, and impersonation attempts than ever before.
At the same time, workforces are more distributed, devices are more diverse, and identity signals are harder to trust.
The result is clear: traditional MFA is no longer enough in high-risk moments. To defend against modern threats, organizations must go beyond passcodes and push notifications. They need a way to verify identity, not just knowledge or possession. In this post, we’ll explore how biometric verification fills that gap, and how iProov’s approach helps organizations adapt to today’s threat landscape without adding friction for legitimate users.
What Is Risk-Based Authentication?
Risk-based authentication (RBA) is a security approach that dynamically adjusts authentication requirements based on contextual risk signals, such as device reputation, geographic location, time of access, or behavioral anomalies.
When activity appears low-risk, users are granted seamless access. But when something deviates from the norm, such as a login attempt from an unfamiliar country, RBA triggers additional verification steps.
This adaptive model strikes a balance between security and user experience, helping to reduce friction while making it harder for attackers to succeed, even if credentials are compromised.

The Role of Risk-Based Authentication in Zero Trust
RBA isn’t just a convenience feature – it’s a key pillar of a Zero Trust security framework. Zero Trust assumes no implicit trust, no matter the user, device, or network. Every access attempt must be verified, continuously and contextually.
By evaluating risk in real time, RBA enables you to:
- Enforce stronger verification for high-risk access
- Minimize friction for low-risk users
- Continuously validate identity beyond the login event
It creates a dynamic access control model that adapts as risk changes, aligning closely with Zero Trust principles.
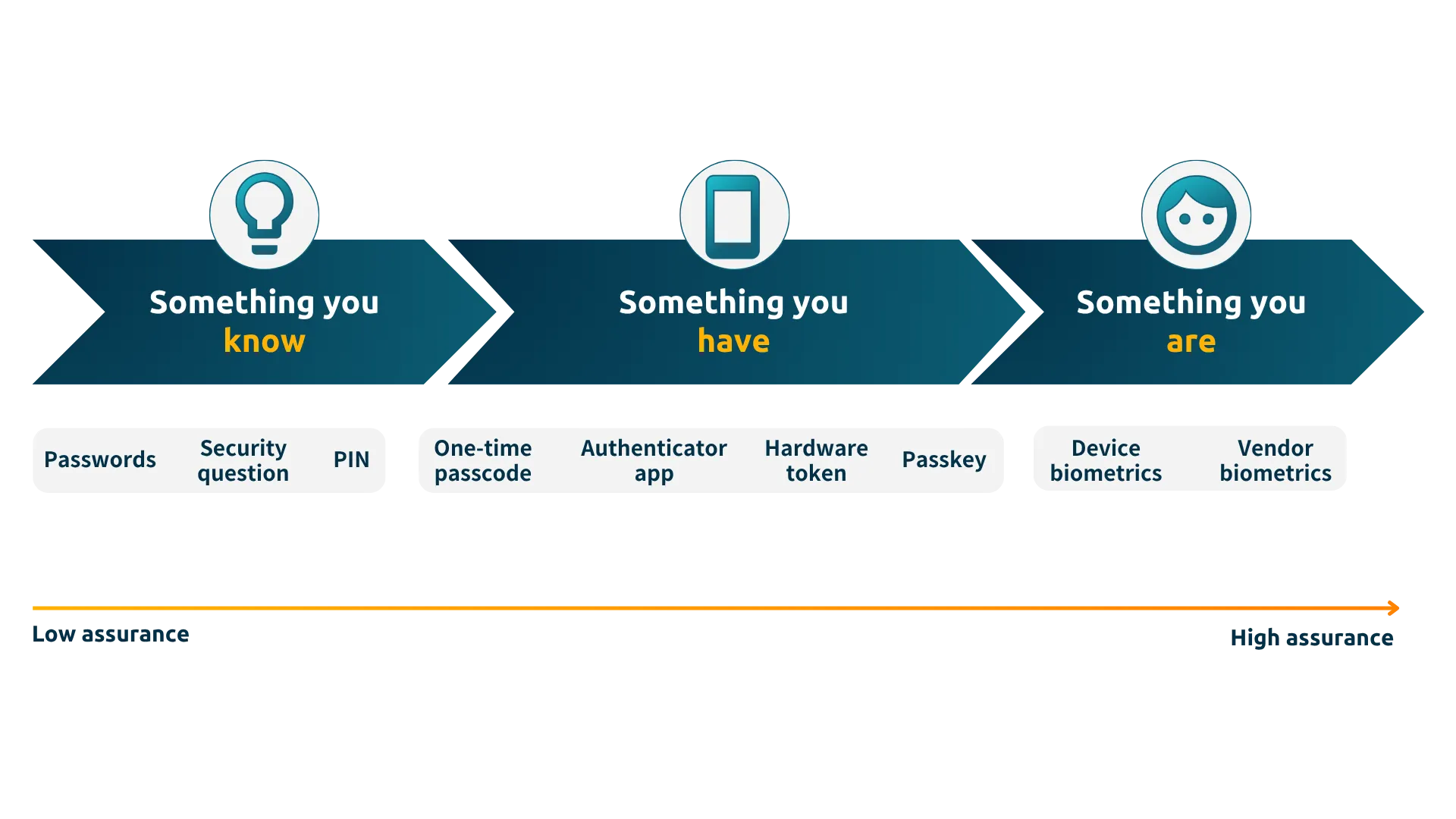
The Problem With Traditional MFA
Risk-based authentication is a smart solution to the security vs speed tradeoff. However, its effectiveness is often undermined by weak step-up authentication methods. Most organizations still rely on OTPs, push notifications, or security questions – all of which can be intercepted, manipulated, or socially engineered. Critically, these methods only verify if you know a credential (knowledge) or have access to a device (possession). They don’t verify who you are (inherence).
How Attackers Bypass MFA in Risk-Based Workflows
Threat actors such as Scattered Spider have revealed how vulnerable MFA becomes when it’s disconnected from identity. Their tactics include:
- Phishing credentials through fake login pages or by convincing telecom providers to transfer phone numbers to attacker-controlled SIM cards, allowing them to intercept SMS OTPs.
- Impersonating employees using AI-generated voice clones to trick help desks into sharing MFA codes or authorizing new devices.
- Session hijacking or device emulation to mimic legitimate user environments and bypass risk signals.
- MFA bombing to overwhelm users with repeated push notifications until they approve one out of frustration or confusion.
These techniques succeed because they exploit a common flaw: the assumption that passing MFA means confirming identity. With AI making these attacks faster and more convincing, risk-based authentication must evolve to include stronger, identity-based verification. In high-risk scenarios, verifying possession is no longer enough – you need to verify identity.
Biometrics: The Missing Layer in Risk-Based Authentication
Biometric verification solves the core issue: it verifies that the right person is behind the login, not just someone holding the right device. It’s a critical capability for high-risk use cases, such as:
- Account recovery
- Remote onboarding
- Privileged access management
- New device authorization
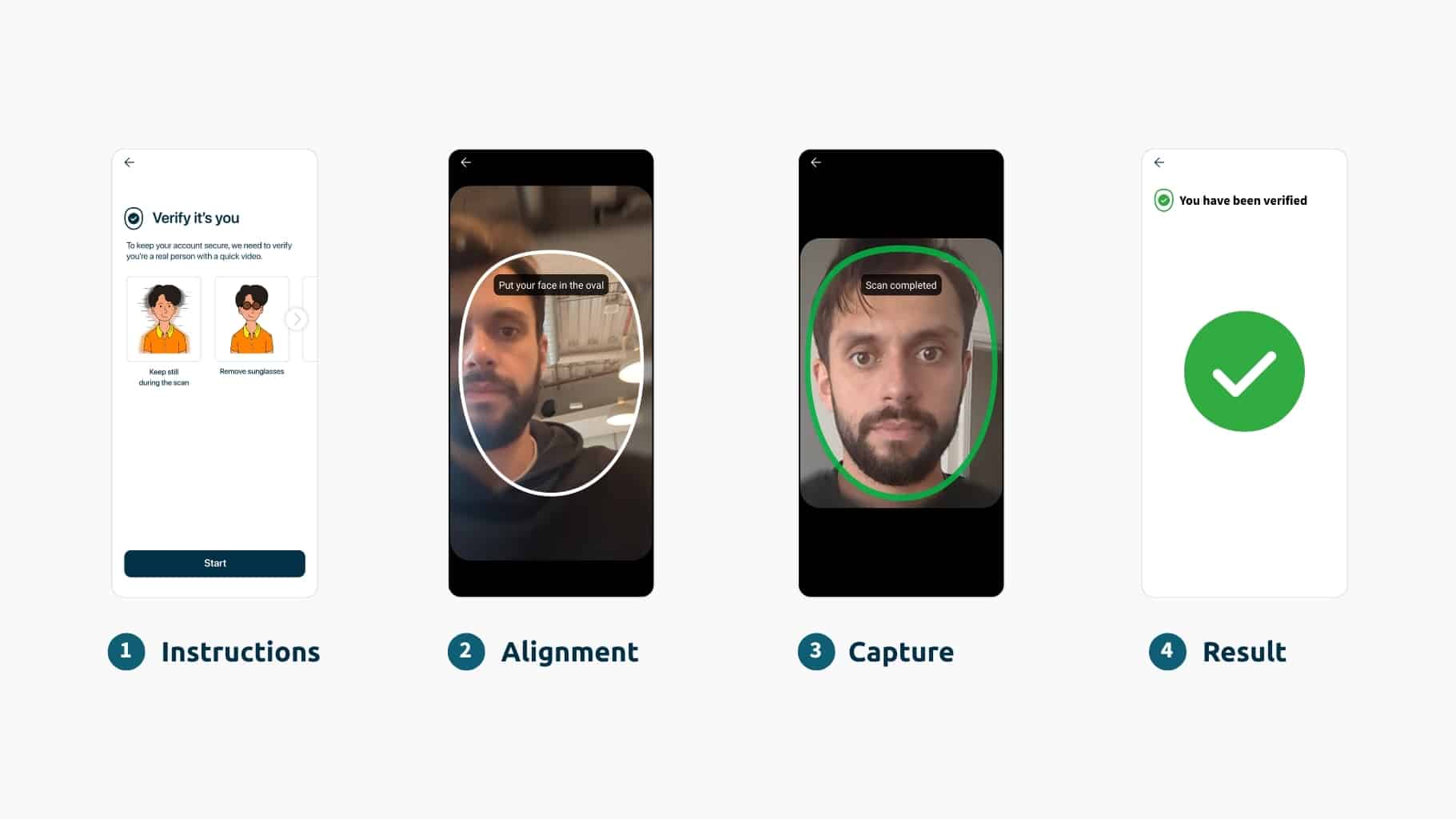
Biometrics ties access to the individual – not the password, phone, or email. It’s resistant to phishing, can’t be intercepted or shared, and when done passively, like iProov’s approach, it adds little to no friction for genuine individuals.
Why Biometrics Outperform Legacy MFA
When added to an RBA framework, biometrics offers distinct advantages:
- Higher assurance: Confirm the actual person, not just a device or token
- Lower fraud: Phishing, spoofing, and deepfakes don’t work against liveness detection
- Better user experience: Passive face verification avoids added steps
- Future-proofing: AI-resistant, cloud-native, and adaptable to evolving threats
Unlike OTPs and push notifications, iProov face biometrics provides resilient assurance even as threat actors evolve their tactics – continuously detecting, adapting to, and defending against emerging attack methods.
How To Strengthen Your MFA Strategy Today
If you’re evaluating ways to close the assurance gap in your RBA strategy, focus on these areas:
- Choose biometrics that verify liveness, not just image matching
- Look for passive methods to reduce user friction
- Prioritize AI-resilient technology that detects deepfakes and adapts to evolving threats in real-time
- Apply biometrics to the highest-risk interactions
- Select vendors that integrate seamlessly with your existing identity stack
Speak to a consultant to explore how biometric authentication fits into your risk-based authentication workflows.