August 30, 2019
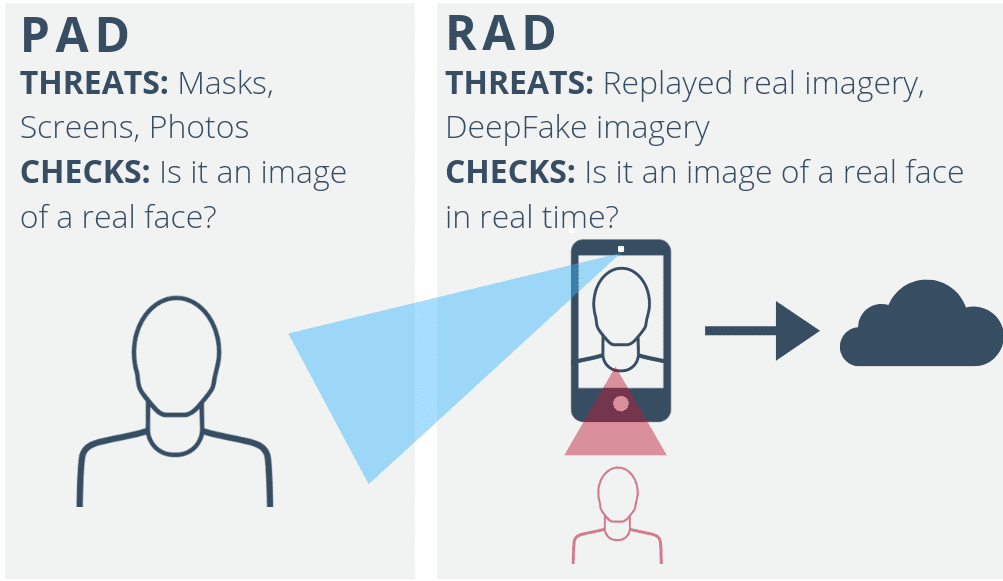
Presentation Attack Detection or “PAD” is a growing topic within the biometrics industry. While this is definitely a step in the right direction, cyber-thieves are still diligently exploiting security gaps in identity proofing and strong customer authentication. Exclusive focus on presentation attacks alone fails to address vulnerabilities to other forms of identity spoofing.
This article will illustrate how PAD alone does not guarantee biometric security. CSOs and Compliance leads must also consider Replay Attack Detection. or “RAD”.
What is Presentation Attack Detection?
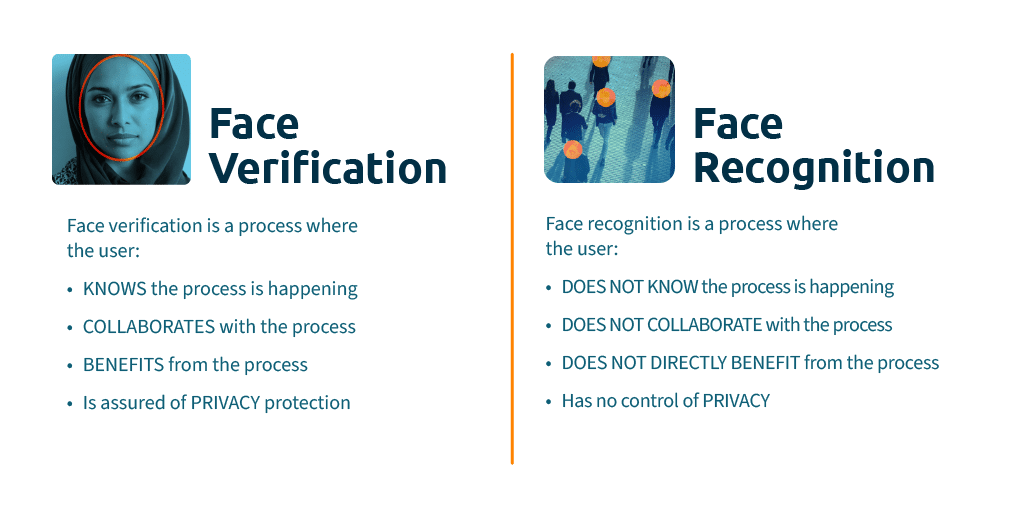
Biometric factors like your face, fingerprint, palm, or iris are inherently different to passwords. This is because their security is not reliant on secrecy. You can find a copy of my face on LinkedIn or Facebook in 3 clicks. You could print out a picture of my face and present it to a face authentication system.
If spoofing identity was simply a case of matching my face with the image being presented, my digital identity would be incredibly unsafe. Rather, biometric security relies on accurately matching a biometric that is genuinely present: the real face. PAD addresses the need for biometric matching to check whether the object that is presented to the sensor is the real biometric as opposed to a physical replica.
Effective PAD will stop someone from printing a photo of my face and holding it in front of my phone’s camera most of the time. It might even stop a $10,000 mask that was made by artisans in Japan using a 3D scan of my face.
The problem is that there are few identity fraud scenarios where the benefit of spoofing someone’s identity is worth the cost of creating a sophisticated mask. The real objective for cyber thieves is to find scalable, low-cost attack vectors which can be rolled out globally across large volumes of victims.
What’s the problem with Presentation Attack Detection alone?
There is an additional but equally critical challenge for biometric security: ensuring there has been no interference from the sensor to the decision processing unit.
What if there is malware affecting the user’s device software or even a full hardware hack? For remote and unsupervised users on their mobile phones, there is always this risk of device compromise.
Browser-based biometric security methods are particularly vulnerable to camera pipeline hijack. This is because the operating system has no control over access to the real camera. Virtual webcam freeware allows users to inject imagery into the application whose real source is totally indistinguishable to the application.
In these cases, the digital service provider cannot be sure exactly how or when the information that reaches its servers was recorded. This means that imagery could be recorded from a successful claim, then retained. At the right moment, that image or video is injected into the application or directly into the network server connection – bypassing the camera entirely. This is a replay attack and it would pass any PAD security. A replay attack is qualitatively indistinguishable from a video of a genuine biometric.
Similarly, device malware can record imagery from the device camera during a successful authentication claim and later be replayed programmatically. This method is incredibly attractive for cyber thieves as it is easily scalable. Once the exploit has been found to work, it can be scaled to thousands of users with minimal incremental cost.
To summarise, PAD fails to addresses the question: “Is this a real authentication, recorded right now?” Biometrics with PAD alone cannot determine that a user is genuinely present at the moment of completing the transaction.
What’s Replay Attack Detection?
Replay Attack Detection is an approach that ensures each authentication claim is unique. Therefore a claim is invalid after the first instance it is processed.
RAD must ensure a claim is unique with a codespace of random variables. These variables must have a large enough range, that they are not susceptible to brute force attacks (retrying several variations until the replay version is successful).
Simultaneously, making a claim unique must not put the onus on the user to do something unique and different each time. Reliance on user interaction to create a unique authentication claim vastly reduces completion rates. Users frequently misunderstand instructions, resulting in a high rate of rejection of correct users and therefore user-drop outs.
iProov takes a different approach by timestamping every claim with a passive “FlashMark“. Using the device screen we project a sequence of colors on the user’s face. We then analyze the video to test whether the claim is real or replayed. With a codespace of over 1,000,000 possible combinations, no user will ever receive the same FlashMark twice.
PAD has become topical in recent years. Standards for PAD testing like ISO 30107 and NIST have been introduced. iProov has been found to conform to such standards by the National Physical Laboratory, who found iProov’s PAD technology “state of the art”. At iProov, we’re thrilled that the market is now demanding biometric security which goes beyond accurate matching. However, we will continue to push the boundary and address the holistic security challenges the market is yet to focus on… because those are the security challenges on which the cybercriminals are focused.